The Most Devastating Hack in History! Bybit Exchange Loses $1.5 Billion—How Did North Korean Hackers Breach a Multi-Sig Cold Wallet?

GM,
The world’s second-largest exchange, Bybit, had its multi-signature cold wallet hacked late at night on February 21. Over 400,000 ETH—worth up to $1.5 billion—was stolen. This marks the largest loss in history, 2.5 times greater than the second-largest hacking incident.
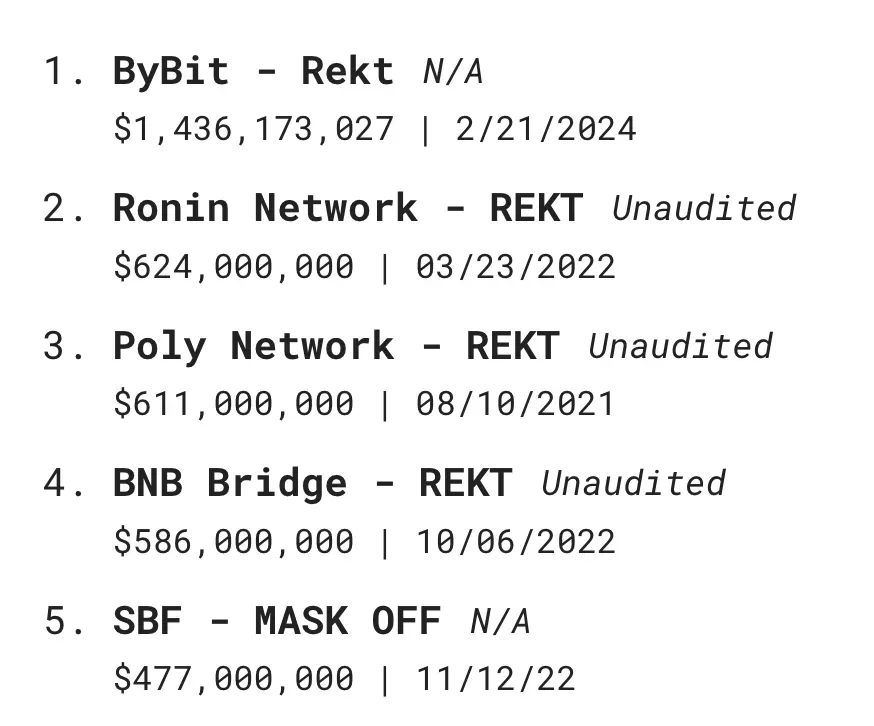
The attack instantly made the thief the 14th largest ETH holder in the world, surpassing Ethereum founder Vitalik Buterin, the Ethereum Foundation, and Ethereum ETF issuer Fidelity.
This was a perfect heist without a single gunshot. Mounting evidence points to North Korea’s state-sponsored hacking group, Lazarus Group, as the mastermind. They bypassed Bybit’s triple-layer security—cold wallet storage, multi-signature protection, and hardware security measures—without ever gaining access to the private keys.
The largest crypto hack in history is far from over. A global manhunt has just begun, with every move broadcast live on the blockchain. The hacker continues shifting funds daily, attempting to launder the stolen assets, while on-chain sleuths worldwide, the U.S. FBI, and Interpol are in relentless pursuit. This article takes you through the gripping events of the past three days.
Exchange Bank Run
Late on February 21, renowned on-chain detective ZachXBT raised the alarm. He noticed an abnormal outflow of $1.46 billion from Bybit and quickly published the suspicious wallet address.
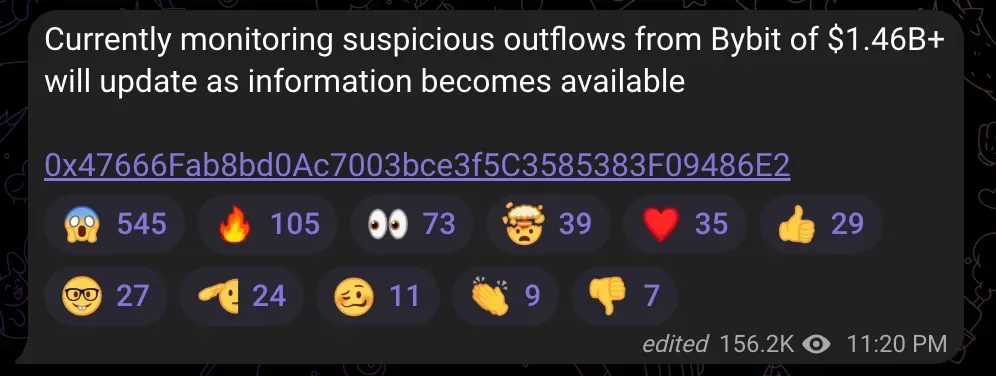
Just four minutes later, Bybit CEO Ben Zhou confirmed that the exchange’s multi-signature cold wallet had been hacked, resulting in the loss of 400,000 ETH. He shared the transaction records, which showed the sender as Bybit’s cold wallet and the recipient as the suspicious address ZachXBT had just flagged. The news spread rapidly across the internet. Blockchain analytics firms quickly set up monitoring dashboards to help investigators track the hacker's latest moves, while users rushed to withdraw their funds, fearing a repeat of past exchange collapses.
Surprisingly, despite the massive loss, Bybit didn’t halt withdrawals. Instead, the company immediately announced that all withdrawal functions would continue as usual. This bold decision shocked experts and became the first major turning point in the incident. While some mocked users who had just received FTX compensation only to deposit it into Bybit, the exchange has since processed nearly $6 billion in withdrawal requests with almost no complaints from users about delayed payouts.
Bybit CEO Ben Zhou emphasized that since it was confirmed the breach targeted the Safe multi-signature cold wallet—rather than the exchange itself—there was no reason to restrict withdrawals. They prioritized processing withdrawals for retail users and VIPs before moving on to institutional clients. This decision not only helped contain the spread of panic but also paved the way for a potential recovery.
Asset auditing firm Hacken quickly released a report assuring that Bybit’s solvency remained intact. But after the FTX collapse, who would trust such claims so easily? Like many others, I decided to withdraw my funds. The money arrived swiftly, restoring a bit of confidence. What was even more surprising was that several transfers—each worth hundreds of millions of dollars—were deposited into Bybit during this turmoil. It defied logic. Who would deposit large sums into an exchange teetering on the brink?
It turned out that these funds came from other exchanges and major asset holders who still believed Bybit wouldn’t fall. They voluntarily provided liquidity support, hoping to help Bybit weather the bank run. Unlike government-led interventions during traditional bank runs, this support was purely community-driven—a testament to the goodwill Bybit had built over time.
In this way, Bybit survived the most critical 24 hours. As the withdrawal frenzy eased, market confidence began to recover, and the world’s “second-largest exchange” temporarily overcame its collapse crisis. But a pressing question remained: how did the hacker manage to breach Bybit’s multi-signature cold wallet?
The Perfect Heist
Bybit CEO Ben revealed that the exchange used one of the strictest security measures—Safe multi-signature cold wallets. Every transaction required multiple administrators to co-sign (e.g., 3 out of 5 signatures), with each administrator using an independent cold wallet.
This setup created three layers of security. Cold wallets ensured private keys were stored offline, multi-signature requirements mandated multiple confirmations, and the hardware devices of these wallets displayed transaction details on independent screens. This combination of technical and social safeguards was meant to be nearly impenetrable under normal circumstances. And yet, hackers still broke through. Why?
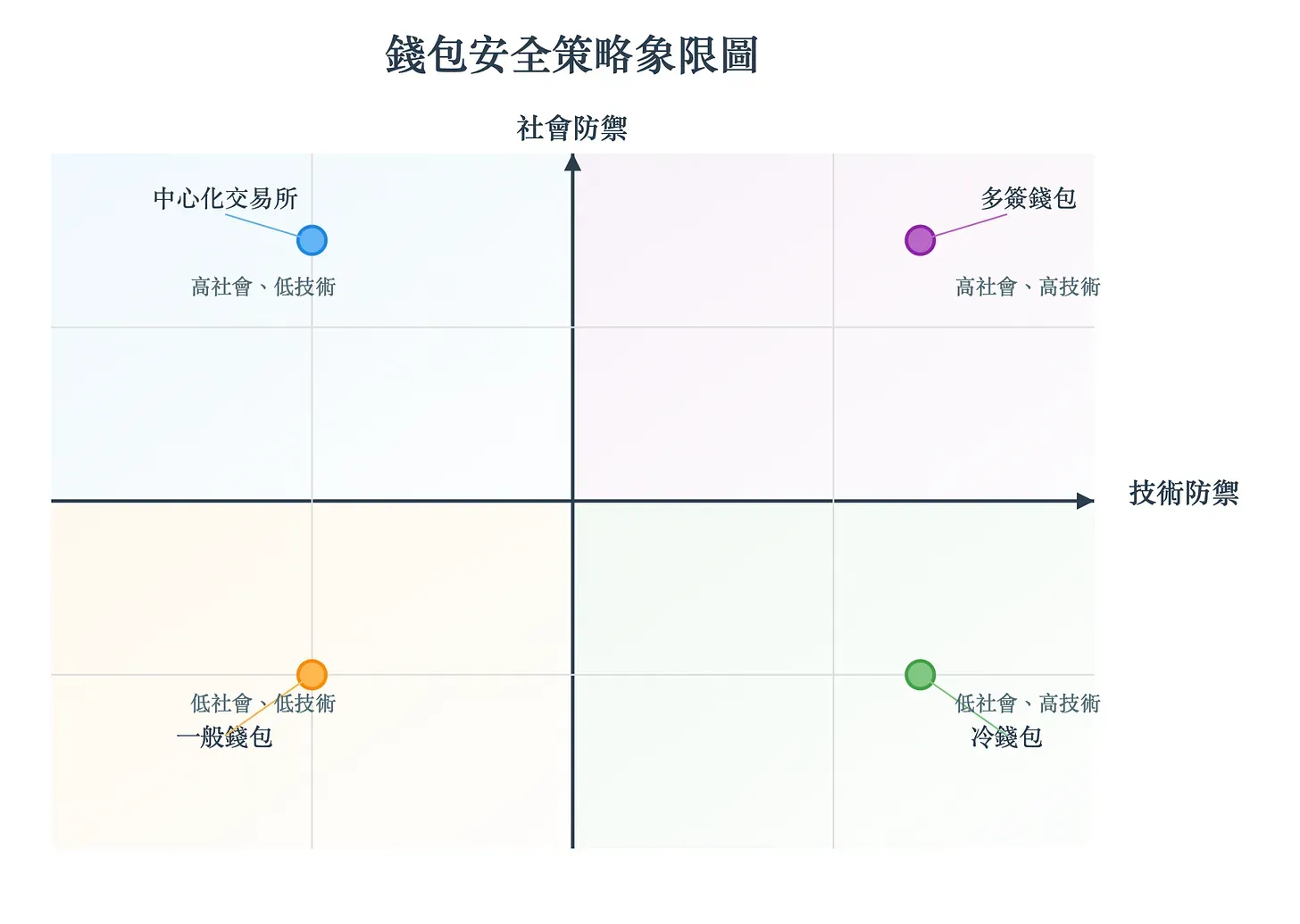
Let me explain the basic process of how a multi-signature wallet operates. For every transaction, one administrator must initiate it and specify the transfer details. The system then notifies the other administrators to review and approve the transaction. Once the required number of approvals is met, the final signer can submit the transaction.
Ben admitted that he was the final signer who approved the hacker's transaction. He recalled seeing what appeared to be a routine notification: transferring 30,000 ETH from the cold wallet to the exchange’s hot wallet. This kind of internal fund transfer typically happens every two to three weeks. Ben carefully checked the URL—it was indeed safe.global—and verified that the recipient address matched Bybit’s hot wallet. Confident everything was in order, he took out his Ledger cold wallet to sign the transaction.
But then, something felt off. The Ledger screen displayed a string of unreadable gibberish, which didn’t match the transaction details shown on the website. Still, because this was a routine operation and he had just reviewed the details on his computer, he dismissed the anomaly and pressed the confirmation button. Thirty minutes later, an emergency alert came through: all 400,000 ETH in the cold wallet had been drained.
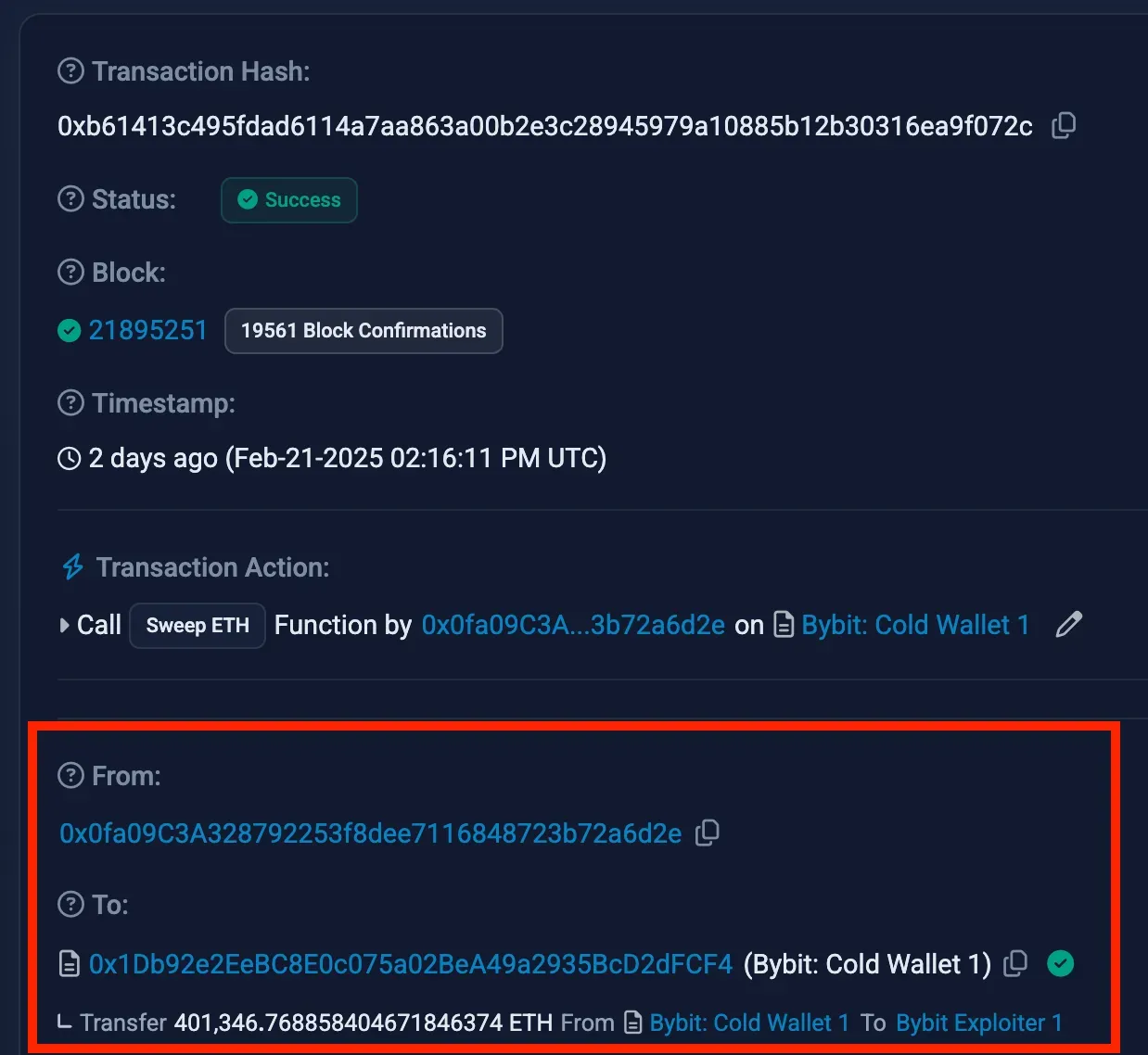
The investigation revealed that the transaction was actually a carefully set trap by the hacker. While it appeared to be a routine transfer, it was, in reality, an authorization change to the multi-signature wallet. The hacker didn’t break in forcefully but took a patient, strategic approach—first seizing control of the wallet before draining all its assets in one swoop. It was like a safe deposit manager thinking they were approving a routine withdrawal but unknowingly signing a document to “change the locks.”
Ben’s first suspicion was directed at Safe’s system. Could their servers have been compromised, leading to a mismatch between the displayed transaction details and the actual ones? Safe didn’t take any chances—they immediately shut down the front-end interface and launched an internal investigation. So far, they haven’t found any signs of a breach. A more likely scenario is that Bybit’s administrators were targeted in advance, with their computers compromised to display fake transaction details.
This explains why the data Ben saw on his Ledger device didn’t match what appeared on his computer screen. CoolWallet CEO Michael Ou has repeatedly emphasized1 that if a cold wallet’s screen displays different information from the computer, you should never sign. Unfortunately, Bybit’s administrators ignored this critical warning and fell into what cybersecurity experts often call the trap of blind signing.
Several key questions remain unanswered:
- Who initiated the malicious transaction?
- What exactly did they do when setting it up?
- How did the hacker know the precise timing of Bybit’s routine fund transfers?
- Most importantly, did the other administrators carefully verify the transaction before signing?
But the most urgent task now is to identify the hacker and stop them from laundering the stolen funds.
The Hacker Reveals Themselves
What followed was a global, real-time cat-and-mouse chase. The hacker who stole 400,000 ETH was highly skilled and had one clear objective: evade tracking and cash out the crypto. To achieve this, they went to great lengths to obfuscate the money trail—but ironically, these complex maneuvers began to expose their identity.
Immediately after the theft, the hacker split the stolen ETH into 40 separate wallets, each holding exactly 10,000 ETH. From there, they employed multiple strategies. Some of the stolen funds were swapped through decentralized exchanges (DEXs) to convert potentially frozen tokens into untraceable ETH. Other portions were bridged to different blockchains like Bitcoin, Solana, and Avalanche using cross-chain bridges. Today, the stolen assets are scattered across 920 different wallets. But with every transfer, they left behind more clues.
Investigators discovered that some of the wallets receiving the stolen funds were previously linked to North Korea’s Lazarus Group, a notorious state-sponsored hacking team. Even more surprisingly, one of the hacker’s wallets was traced back to an account that had previously launched a popular meme coin on Solana.
This revelation was eye-opening. It turns out that the Lazarus Group isn’t just skilled at hacking exchanges—they also exploit the hype around meme coins to scam investors. Speculators hoping to get rich off meme coins unknowingly became accomplices in the hackers' money laundering scheme. However, their plan hasn’t gone entirely smoothly. Amidst global efforts to block the stolen funds, 15,000 ETH and 180,000 USDT have already been frozen. Several exchanges have pledged to help intercept the stolen assets, and some have even suggested forking Ethereum as a last-ditch effort to recover the losses.
At this point, everyone is asking the same question: Are North Korean hackers really this good? Sun, the Chief Security Officer at XREX, once pointed out that Lazarus Group’s greatest strength lies in social engineering. In other words, they don’t always exploit technical vulnerabilities—they exploit human weaknesses. This incident proves that even the most secure multi-signature cold wallets can’t fully defend against social engineering tactics.
Had Bybit CEO Ben paused and asked his engineers to double-check when he noticed the mismatched data on his Ledger device, this $1.5 billion catastrophe could have been avoided. But the routine nature of the transaction lulled him into a false sense of security, ultimately leading him to open the vault door for the hackers himself.
Lazarus continues to succeed in major international hacking incidents not just because they are technically skilled, but because they masterfully exploit human psychology. They aren’t just a hacking group—they’re a fraud syndicate that weaponizes trust.
Blocktrend is an independent media platform sustained by reader subscription fees. If you find Blocktrend's articles valuable, we welcome you to share this piece. You can also join discussions on our member-created Discord or collect the Writing NFT to include this article in your Web3 records.
Furthermore, please consider recommending Blocktrend to your friends and family. If you successfully refer a friend who subscribes, you'll receive a complimentary one-month extension of your membership. You can find past issues in the article list. As readers often inquire about referral codes, I have compiled them on a dedicated page for your convenience. Feel free to make use of them.



