GM,
It's currently the voting period for Gitcoin Grants. If you wish to participate in this round of quadratic funding, you can start by verifying your identity on Gitcoin Passport. Once you have accumulated a score of 20 points or more, you can proceed to Gitcoin Grants. There, you can cast micro-donations (recommended at around $1.5 USD or 0.001 ETH equivalent) to support the projects you admire.
Blocktrend relies on everyone's backing, and it's also encouraged to keep an eye on the real-time tally of votes. Now, let's get to the main topic.
Have you ever received almost a 0-dollar transfer in your personal wallet or exchange account without any apparent reason? If no one comes to reclaim that amount afterward, you should be cautious. It's not a free lunch (in fact, the amount isn't even enough for a meal); rather, your wallet address or exchange address has become a target for hackers.
Don't panic just yet. It's not due to your operational mistake; it's simply that hackers are casting a wide net, effectively shooting in the dark. Over the past few months, I have received such transfers multiple times, luckily without falling into the trap. It wasn't until recently that I realized, oh, these were all sweetened poisons sent by hackers.
This article discusses why hackers distribute cryptocurrencies through airdrops, whether anyone actually falls for them, and how we can protect ourselves.
Zero-Dollar Phishing
The image below shows the transaction history of my wallet. In March of this year, I transferred 500 USDT from my wallet to an exchange. That's the transaction indicated by the white text "-500 USDT" at the bottom of the image. Within seconds, my wallet received another transaction of "+0.0005 USDT." At the time, I found it a bit odd. I had clearly sent money out, so why would the exchange send money back? And why such a small amount? But since the 0.0005 USDT was a minuscule sum (approximately 0.015 NTD), I didn't bother to investigate further.
In the following months, similar situations occurred repeatedly. Whenever I made a cryptocurrency transfer, I would almost instantly receive small amounts of spare change. The most recent occurrence was just last week when I received two incoming notifications at once. Although the total of these two transactions was less than 1 NTD, my curiosity was piqued— who was randomly distributing money, and what was their motive?
As it turns out, these funds were all lures set by hackers. Let's take the example from the image above. When I made the 500 USDT transfer, the receiving address started with 0x2E2c and ended with 725D. Coincidentally, the 0.0005 USDT that entered my wallet seconds later also originated from an address that started with 0x2E2c and ended with 725D. Without careful observation, it's easy to mistake it for a refund from the exchange, just as I did.
However, these two addresses are not the same; they just look extremely similar. If you look a few characters further, you'll notice that the exchange's address starts with 0x2E2c4, while the wallet address that received the micro-payment starts with 0x2E2c8. A single digit difference in a phone number means you're talking to a different person. Similarly, a one-digit difference in a transfer address means it's meant for someone else. This is the carefully crafted phishing scheme designed by hackers.
This month, a senior employee from Binance, a prominent exchange, fell into a trap while managing internal funds and inadvertently transferred up to 20 million USD worth of USDT into a hacker's wallet.
Attack Method
According to Changpeng Zhao (CZ), the CEO of Binance:
"I'd like to share a very clever and almost successful scam that happened yesterday. We managed to retrieve $20 million, and I hope this experience can help you in the future. Hackers are now incredibly skilled; they can generate phishing addresses with the exact same starting and ending letters. And this is the information most people check when conducting cryptocurrency transfers.
In reality, many wallets use '...' to hide the middle content of an address, making the user interface cleaner. However, hackers maliciously exploit this feature to send you fake transactions, causing their phishing addresses to appear in your wallet. If you later want to make a transaction, you might directly copy the address from your previous transaction. At this point, you could accidentally copy a phishing address that the hackers gave you, one that looks very similar. This is an actual incident that occurred to an experienced cryptocurrency user just yesterday. Fortunately, the user immediately noticed the mistake, and we promptly requested a fund freeze. The hackers did not get away with those funds."
I've used a cash flow tracking chart to recreate the thrilling process where Binance almost lost $20 million. The five blocks on the left side of the image, from top to bottom, are Binance's hot wallet addresses, with the middle block being Binance's fund dispatch relay station. The block on the upper right is the destination of the fund dispatch, likely a cold wallet for fund storage. The block on the lower right is the hacker's wallet address.
Starting from July 14th, the Binance employee began transferring a total of up to $169 million worth of USDT from the relay station to the cold wallet, as shown in the top-right corner of the image. However, on August 1st, during the process of dispatching $20 million, the Binance employee accidentally transferred the funds to the hacker's address in the bottom-right corner.
Upon closer inspection, you'll notice that the phishing address in the bottom-right corner and the cold wallet address in the top-right corner appear remarkably similar. Both addresses start with 0xa7b and end with 90570. If you focus only on the starting and ending parts, it's easy to mistake the two as the same address. From CZ's description, it can be inferred that this seasoned Binance employee likely directly copied the address from a previous transaction without careful verification, which led to inadvertently stepping into the trap.
However, Binance acted swiftly, and they certainly had a direct communication channel with the USDT issuer, Tether. As a result, approximately 50 minutes after the incorrect transfer occurred, the $20 million worth of USDT was forcibly frozen by Tether.
On the other hand, the hackers were considerably slower, not realizing they had caught a big fish until about an hour after the USDT was frozen. At that point, they hurriedly tried to convert some ETH to withdraw the USDT, but the funds were already locked down.
It's fortunate that this time the victim was Binance, able to prompt Tether to freeze the assets within an hour. If the scenario involved you or me, by the time we became aware of the hack, sought help through layers of intermediaries, the hackers would likely have already converted the USDT into other cryptocurrencies and made their escape.
Some might ask, it makes sense for hackers to target Binance's wallets due to the significant transaction volume, but why would individual users like us also become targets of this zero-dollar phishing scheme?
Preventive Measures
Coinbase has dissected this zero-dollar phishing technique, breaking down the hackers' attack into three stages: search, bait, and wait.
During the search phase, hackers write programs to monitor every action on the blockchain, targeting wallet addresses that have recently made transfers. The records on the blockchain are public and transparent. Hackers observe where these individuals are sending their money and immediately generate phishing addresses that are very similar in structure.
Next, hackers deposit a small amount into this phishing address and send some of that small amount to potential victims. This step needs to happen as quickly as possible. Many people are completely unaware that a transaction has just come in and might mistake it for their own operation.
Finally, the hackers wait. Although from the user's perspective, the directions of sending and receiving are completely opposite, so there shouldn't be any confusion. However, because the phishing fake address generated by hackers looks so similar to the real one, if a user isn't paying close attention, they might inadvertently transfer their assets to the hacker's pocket.
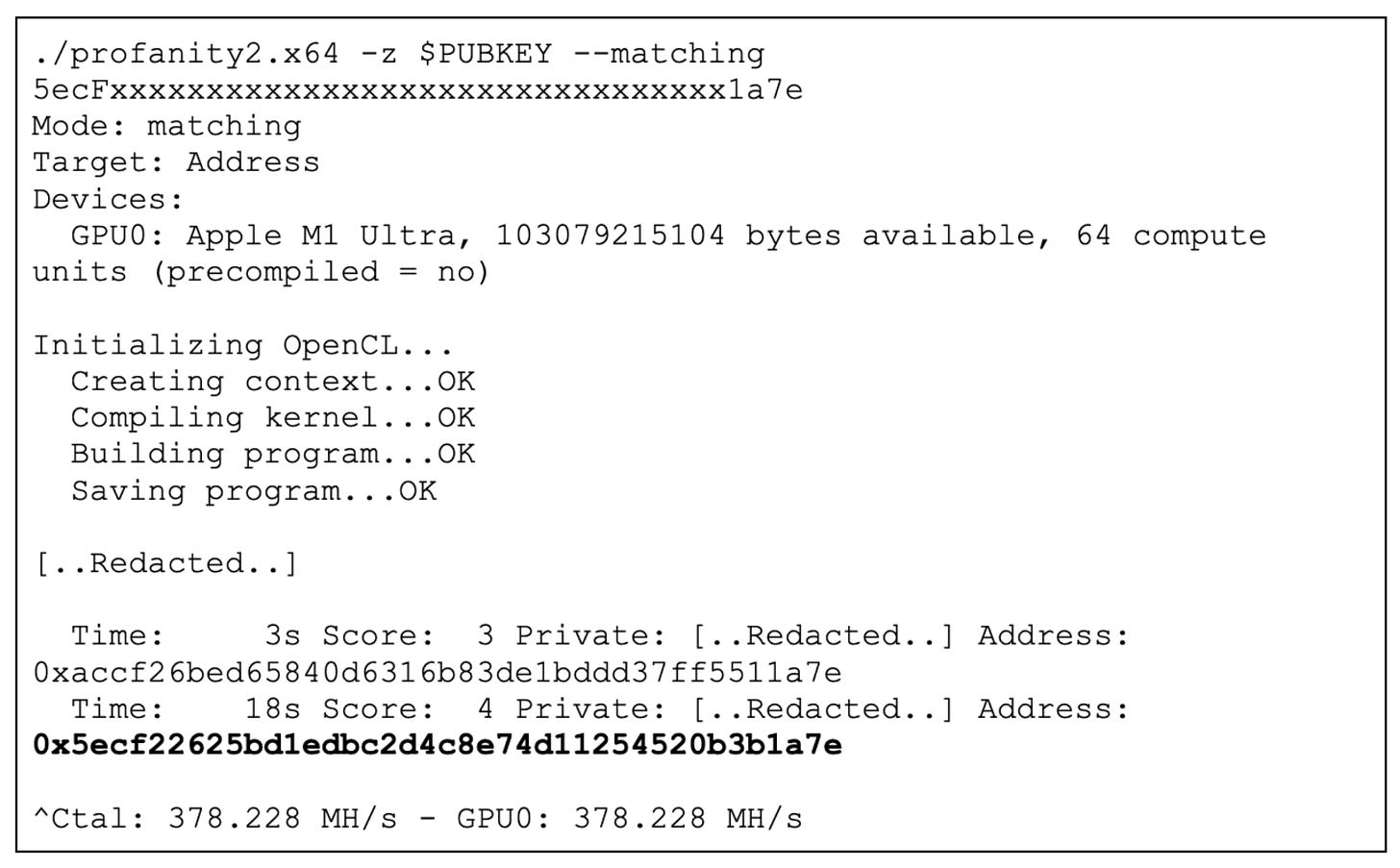
Many might wonder, is it really so easy for hackers to generate addresses with the same starting and ending characters? Coinbase conducted an experiment to show this. They used Apple's M1 Ultra chip and a free tool called Profanity2 from the internet. With these tools, they were able to generate wallet addresses with the same last 4 characters in just 3 seconds and addresses with the same first and last 4 characters in just 18 seconds. It's astonishingly fast.
Hackers just need to combine monitoring and baiting processes using automated tools to create the peculiar situations you encountered initially.
However, such attacks do come with their own costs. Every time a hacker deploys bait, they need to pay a blockchain miner's fee. Consequently, phishing activities are more rampant on blockchains like Tron, Polygon, and Binance Smart Chain, where transaction fees are lower.
Towards the end of last year, cybersecurity firms issued warnings about this "zero-dollar phishing airdrop," but as of now, there are still no foolproof countermeasures. After all, transferring funds on the blockchain is a matter of personal freedom, and hackers can even argue that they're conducting an airdrop. Who would suspect receiving a "gift"? It's challenging to determine whether users sending funds to the wrong address can be classified as being "hacked."
For now, the most effective approach lies with the users themselves. Many wallet apps now come with a built-in contact feature. By adding your frequently used wallet addresses to a whitelist, you can safeguard against phishing addresses created by hackers, no matter how similar they appear. Additionally, taking advantage of the recent bear market in the cryptocurrency industry and lower Ethereum gas fees, you can rent your own ENS domain name. Using something like "mnhsu.eth" as your wallet address is much more memorable than "0x36F322fC....E2b38381."
This not only increases your real-score on Gitcoin Passport but also reduces the risk of accidental errors in future transactions.
Blocktrend is an independent media outlet sustained by reader-paid subscriptions. If you think the articles from Blocktrendare good, feel free to share this article, join the member-created Discord for discussion, or add this article to your Web3 records by collecting the Writing NFT.
In addition, please recommend Blocktrend to your friends and family. If you want to review past content published by Blocktrend, you can refer to the article list. As many readers often ask for my referral codes, I have compiled them into a single page for everyone's convenience. You are welcome to use them.