GM,
Recently, there has been frequent mention of on-chain transaction tracking in the Blocktrend. For example, ZachXBT, an on-chain detective who analyzes on-chain transactions, was sued by Jeffrey Huang. On Tuesday’s discussion of the Gitcoin Grants witch attack, I also used visualization tools to transform complex on-chain data into clear transaction flow diagrams. In yesterday’s podcast, guest Lindy also introduced three on-chain transaction analysis tools—OKLink, MistTrack, and BitQuery.
But if you find all these three tools too complicated, this article will introduce MetaSleuth, which is currently my favorite all-in-one on-chain transaction analysis platform, and it is free to use. In this article, I will use recent fraud cases as examples to explain how MetaSleuth can help everyone avoid scams, assist friends in emergencies, and even provide valuable information for law enforcement.
But what if you find all three tools too complicated after reading about them? The MetaSleuth, which I'm going to introduce in this article, can be said to be my favorite one-stop on-chain fund flow analysis platform, and it's currently free to use. In this article, I will use a recent fraud case as an example to illustrate how MetaSleuth can help you avoid losses, assist your friends in emergencies, and even provide useful information for law enforcement agencies.
Crime proceeds flow
Recently, I heard a terrifying case of cryptocurrency theft that a friend shared with me.
The victim of the incident was unknowingly implanted with malicious software by hackers in their computer. The program is very clever and will secretly replace the contents of the clipboard with the hacker's wallet address whenever it detects the user copying a cryptocurrency wallet address, such as an Ethereum address starting with 0x. If the person making the transfer doesn't double-check when using the MetaMask wallet, they will transfer the funds they intended to send to a friend or exchange directly into the hacker's pocket.
Usually, it takes some time for the recipient to realize they haven't received the payment and for the victim to discover that they've sent the funds to the wrong address. This leads to a moment of panic, and the victim may not even know whether reporting to the authorities will be of any use. Reporting to the authorities is done to recover the assets through the power of the state. However, in the future, if victims ever unfortunately encounter similar incidents, they can use MetaSleuth to quickly locate where the funds are flowing.
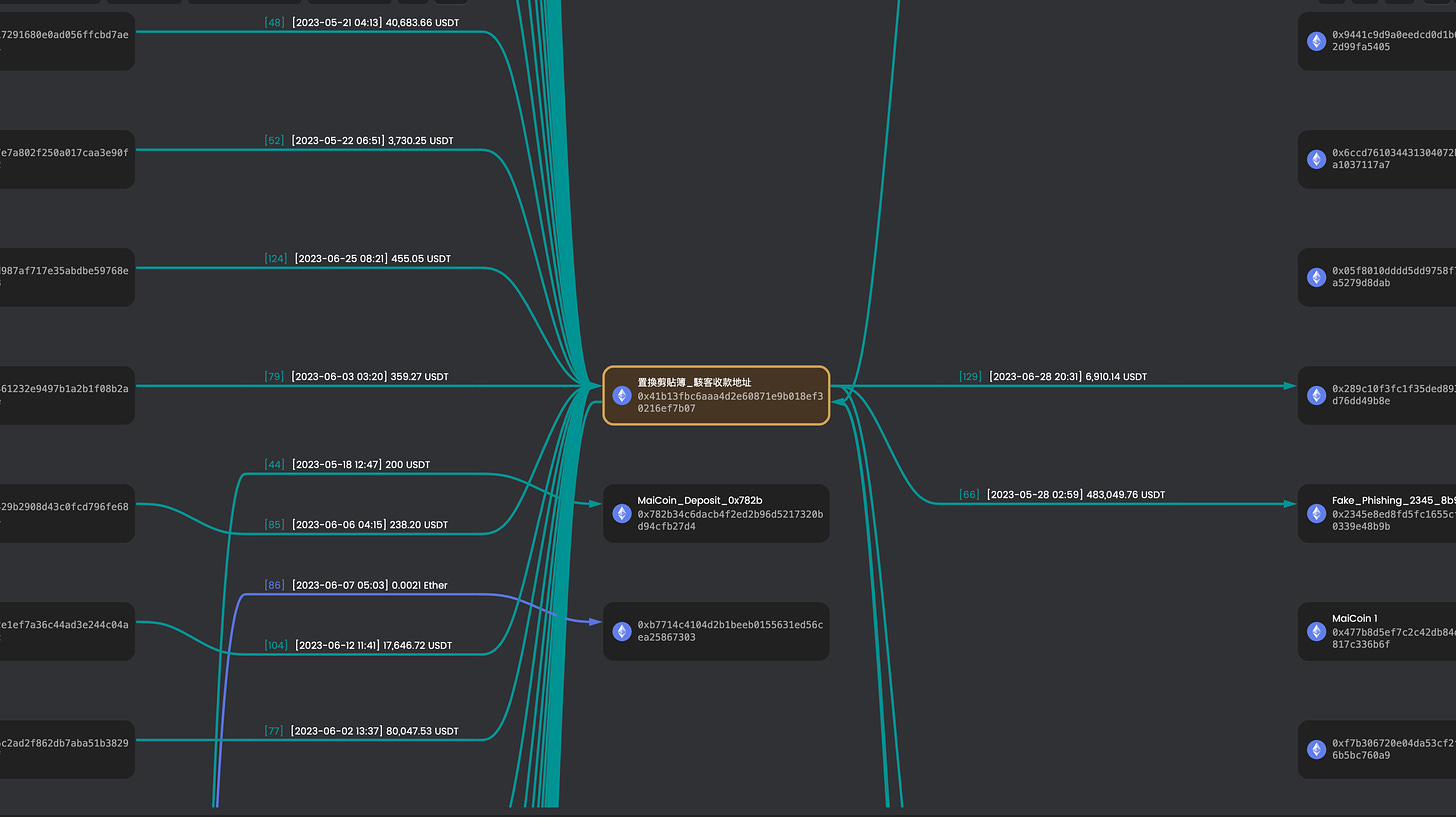
In the case of this incident's victim, they originally intended to transfer the assets in their wallet back to the exchange but had their clipboard replaced by the hacker, with the receiving address changed to 0x41B13FbC6aAA4D2E60871e9B018ef30216Ef7b07. I put this address into MetaSleuth for analysis and obtained the following results. You can view it on your computer to see it more clearly; otherwise, the font may be too small.
Since the end of April this year, the hacker's wallet address has received nearly 590,000 USDT (about 18 million TWD) from the first successful transaction of 300 USDT. The latest victim appeared two days ago, transferring 9,355 USDT to this wallet. Seeing the amount, we can understand why the hacker is willing to take risks.
However, having just the wallet address is not enough to retrieve the funds. One must also determine who the address belongs to since anyone can create a wallet address on the blockchain. By buying a second-hand phone and connecting to public WiFi, a hacker can easily create numerous anonymous receiving addresses and wait for people to fall into their trap.
To identify the actual owner of this address, one can trace the inflow and outflow of funds to the wallet address. Assets do not appear out of thin air; if the hacker's wallet does not contain any ETH as a transfer fee (gas fee), they cannot transfer the USDT that they obtained. Therefore, one direction is to track who transferred the ETH to this wallet address. Additionally, hackers usually want fiat currency in the end, and there are still very few stores willing to accept cryptocurrency payments. Thus, another approach is to observe where these USDT go to be cashed out.
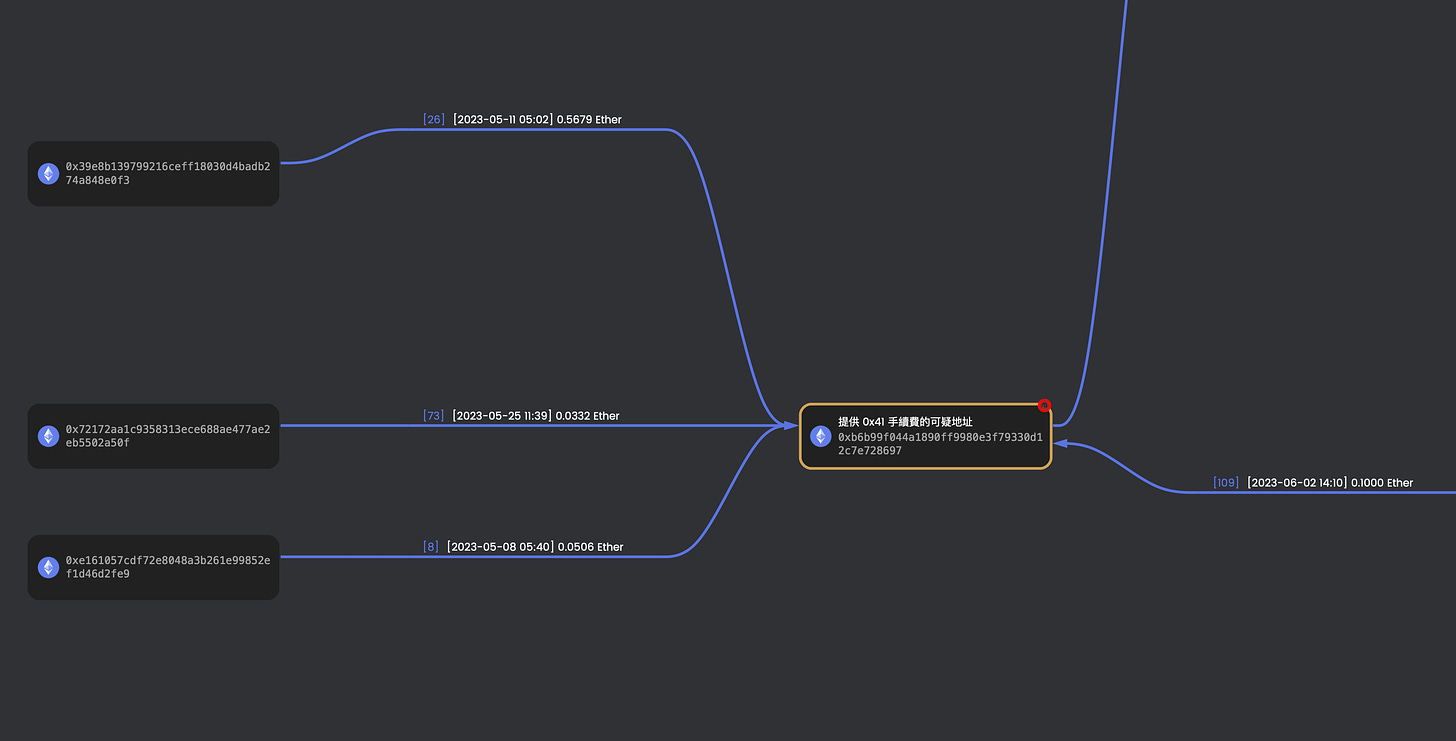
After applying the first method, it turns out that the result is unexpectedly straightforward. From the figure below, there is only one wallet address starting with 0xb6 before and after, which transferred 0.1 ETH to the hacker's address on May 12th. This is the simplest fund flow and can be further traced upward.
When we trace where the ETH comes from starting with wallet address 0xb6, we will find that the fund flow source becomes more and more complicated. There are four other wallets that transferred ETH to the wallet address starting with 0xb6. These wallets may belong to the hacker or accomplices, but they could also belong to other victims.
If you continue to trace upwards, you will most likely end up finding that the source is the address of certain centralized exchanges. Since centralized exchanges require real-name verification, the police can usually track down the real person. However, don't get too excited too soon. The further the money flow goes and the more complex the transactions in between, the harder it becomes to determine whether the account holder of the exchange is truly related to the hacker. They might just be a front or someone who, like the victim, has been exploited by the hacker.
If there are no leads when tracing upwards, you can change direction and follow the hacker's wallet address along the money flow to see where this USDT ultimately gets cashed out. This hacker address, 0x41, has received a total of 590,000 USDT over this period, but 580,000 USDT has already been transferred out. Eventually, you can also find some exchange or wallet addresses. However, it's still not easy to determine the relationship between the account and the hacker.
Experienced law enforcement officers may be able to find clues from the blockchain data, but ultimately they have to return to the physical world to clarify why the hacker's funds ended up in certain people's accounts. If it's a front account, who is the actual buyer, and where does the fiat currency flow? These are within the jurisdiction of public authorities.
For those who have been scammed out of cryptocurrency, in the past, they could only search for a needle in a haystack in the Etherscan blockchain browser. Understanding the data on Etherscan in a short amount of time is very difficult without a certain understanding of the blockchain. However, MetaSleuth visualizes the on-chain data. The data source behind it is still the blockchain, but users can simply follow the money flow downward to quickly find out where the assets are currently located and provide this information to the police when filing a report.
This tool can not only help friends and family around you but also be used when you encounter scam messages in the comment section of a Facebook fan page. You can take the address and investigate how the money flow moves after it's received and how it eventually gets cashed out.
MetaSleuth is an advanced tool for tracking money flow and is used when an actual event occurs. However, the same team has also launched another practical browser extension component called MetaDock, which, once installed in your browser, adds labels and annotations to Etherscan pages. It's like installing Whoscall on your phone to identify callers.
MetaDock
According to the description of MetaDock:
MetaDock is a powerful browser extension tool designed for the crypto community. It seamlessly integrates various innovative features and information into blockchain browsers and dApps to provide a more comprehensive user experience. Currently, MetaDock supports Chrome, Edge, Firefox, Safari, and Brave browsers.
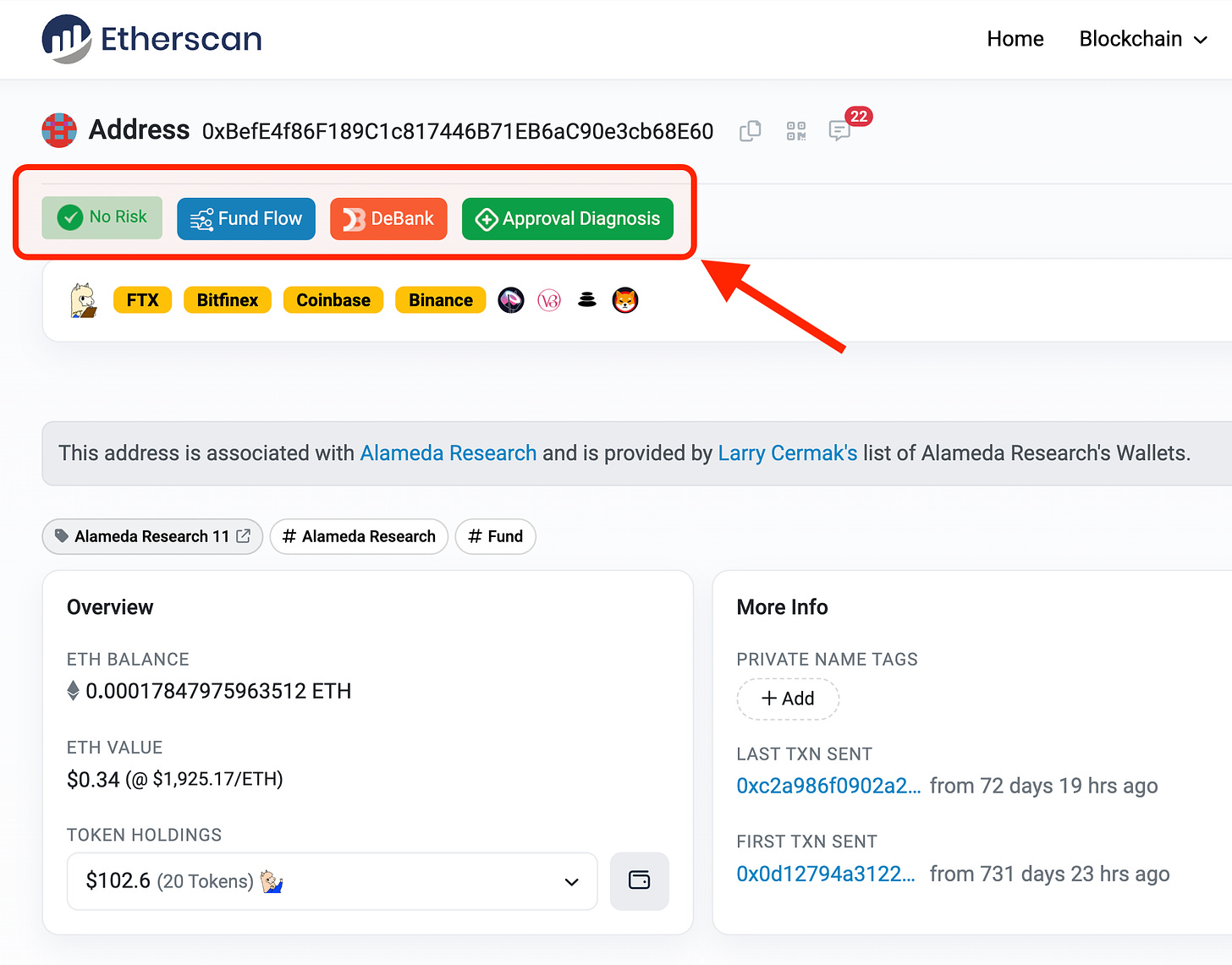
If MetaSleuth can be used to access the call records of money flow on the chain, then MetaDock is like Whoscall in everyday life, helping everyone avoid potential risks. In the example below, I took the wallet address of Alameda Research, which has already closed down. The information within the red box is the additional information provided by MetaDock.
It will add some labels to wallet addresses, for example, the green label on the far left says "No Risk." This doesn't mean absolute safety; it could simply indicate that there are no suspicious reports in the current database, as hackers often switch to new addresses. The "Fund Flow" function is similar to a simplified version of MetaSleuth, where clicking on it allows you to see the inflow and outflow of funds for that address. Debank allows you to see the distribution of assets for that address on different chains. "Approval Diagnosis" is used to check which assets and smart contracts the address currently has authorized access to.
In simple terms, MetaDock adds more information to the platforms users are familiar with. It's like installing Whoscall, where incoming calls are no longer just a string of numbers but can be pre-judged based on the labels provided by other users.
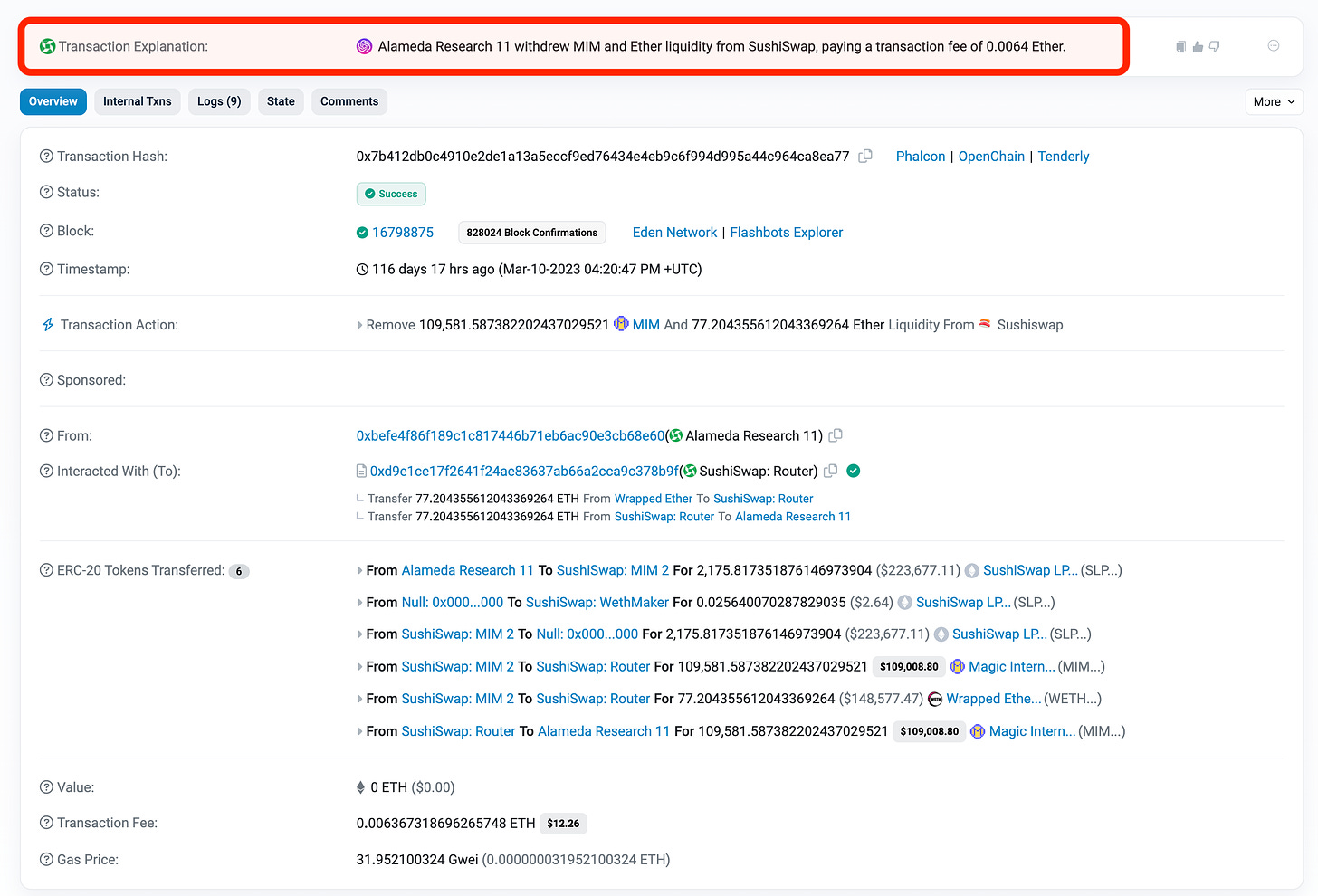
Additionally, MetaDock integrates AI to help translate the cold transaction records on Etherscan into "human language." Previously, it would take some time for people to understand complex transaction details on Etherscan. But now, AI automatically translates the following data into plain language: "Alameda Research's address 11 removed liquidity for MIM and ETH from SushiSwap and paid 0.0064 ETH as transaction fees."
MetaDock is a tool that is particularly helpful for investors. For example, if you receive airdrops of tokens or NFTs out of the blue and are unsure if they are phishing or scams, you can trace back through the transaction records to see if the sender has any risk labels or suspicious behavior. With the combination of MetaSleuth and MetaDock, users will be able to navigate the crypto space more safely.
However, seeing such a useful free tool on the internet, I became curious about how the company behind it plans to monetize it. Surprisingly, it comes back to the concept of public goods crowdfunding.
BlockSec Company
Both of these tools mentioned in the article are created by the blockchain security company, BlockSec. According to their website:
BlockSec is dedicated to establishing secure infrastructure for blockchain. The team consists of top security researchers and experienced experts from industry and academia. We have published multiple blockchain security papers at renowned conferences and have reported zero-day attacks on decentralized finance applications in real-time. We have also successfully defended against attacks, ensuring the security of over $14 million in digital assets.
BlockSec primarily provides security services. They have previously conducted security audits for decentralized exchanges on the Binance Smart Chain such as PancakeSwap, Alpaca Finance, and XY Finance. These DeFi applications handle real money every day, and if there were any security vulnerabilities, the potential impact would be significant. Therefore, pre-security assessments usually come at a high price. This is the main source of revenue for BlockSec.
Today's introduced tools, MetaSleuth may become a paid service in the future, but MetaDock is already open-source and available for free to everyone. The revenue source for free tools is commonly public goods crowdfunding mechanisms like Gitcoin Grants and RetroPGF. MetaDock has participated in the recent round of Gitcoin Grants fundraising and received donations from 102 people, totaling $598. They also received a distribution of $1,064 from the Gitcoin funding pool.
This highlights the importance of public goods crowdfunding mechanisms once again. If this tool operated on a buy-and-sell logic, limiting access to only paying users, hackers would surely be pleased.
However, if it can receive operational funding support through platforms like Gitcoin Grants and RetroPGF, and be freely accessible to everyone, then governments no longer need to spend a large amount of money to purchase money flow tracking tools. Users in the crypto community have already contributed their "on-chain tax money" to fund these tools. Governments can not only directly use these tools but may no longer need to send talent abroad to obtain certifications in on-chain money flow analysis because by then, everyone can be a "keyboard Conan."
After all, the netizens who initiate online manhunts haven't really obtained any licenses, have they?
Blocktrend is an independent media outlet sustained by reader-paid subscriptions. If you think the articles from Blocktrendare good, feel free to share this article, join the member-created Discord for discussion, or add this article to your Web3 records by collecting the Writing NFT.
In addition, please recommend Blocktrend to your friends and family. If you want to review past content published by Blocktrend, you can refer to the article list. As many readers often ask for my referral codes, I have compiled them into a single page for everyone's convenience. You are welcome to use them.