Entering the Zircuit Ecosystem: Predictable Airdrops and Building the Blockchain Hackers Hate
#646
GM,
Over the past few months, what on-chain applications have you tried? Like many others, I’ve found it hard to get excited about most new applications. Partly, I find the mechanisms lack significant innovation; on the other hand, I worry about potential program vulnerabilities, fearing my assets could be compromised. However, Zircuit, the main focus of this article, has brought my wallet back to life because it’s precisely what I’ve been looking for — a way to maximize airdrop opportunities under secure conditions.
When searching for Zircuit online, you’ll mostly find guides on claiming airdrops. But after delving deeper, I discovered that the blockchain’s security features are genuinely worth sharing. I would call it a blockchain with “built-in antivirus software,” and for those worried about asset security, Zircuit’s on-chain applications should be a priority. This article will guide you through the Zircuit ecosystem, highlight its security innovations, and explain where the abundant airdrop opportunities come from.
The Sequencer
Zircuit is another Ethereum Layer 2 (L2) blockchain.
According to data from L2BEAT, there are now as many as 113 Layer 2 blockchains within the Ethereum ecosystem. People have built 113 alternative roads (L2 blockchains) to ease traffic on the main Ethereum “highway,” and this number keeps growing. It’s easy to think, “That’s crazy!” But it reflects that Ethereum is not a centralized company but an open ecosystem that anyone can freely join, with the market weeding out the weak.
How does a new L2 blockchain survive? Being fast and cheap only gets you halfway; to truly succeed, an emerging L2 must excel in a particular area that draws users. Zircuit focuses on safeguarding users’ on-chain assets, offering a built-in “antivirus” of sorts, achieved by enhancing the Sequencer on the L2 blockchain to include AI-driven detection of hacker activity and the proactive revocation of suspicious transactions. But what exactly is a Sequencer?
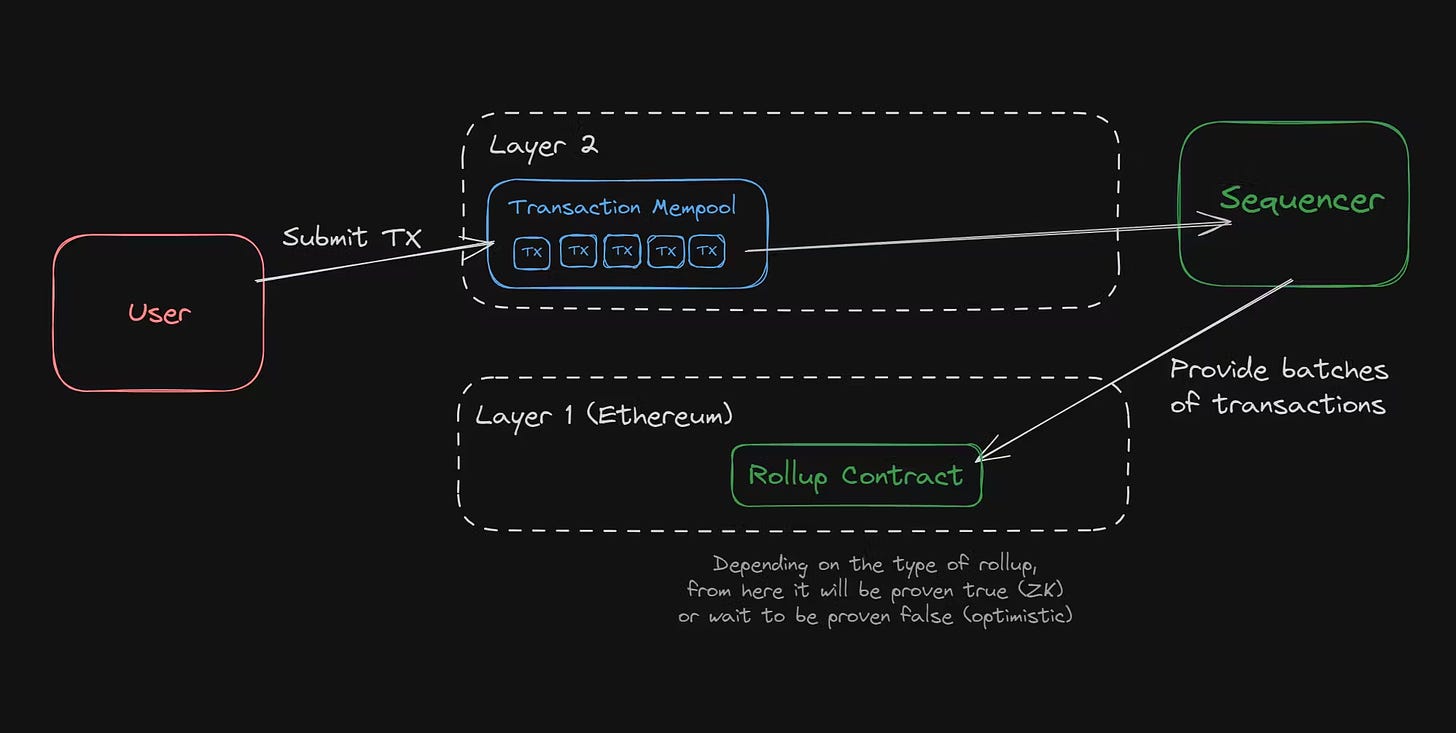
Imagine I walk into a restaurant for lunch, and the establishment accepts cryptocurrency payments via an L2 blockchain. I can then open my crypto wallet and transfer assets to the restaurant’s specified payment address. The transaction will complete in a matter of seconds, much like a seamless LINE Pay checkout. But on-chain, this transaction takes a more complex route within just a few seconds, moving through three locations:
Mempool
Sequencer
Ethereum
The Mempool acts as a waiting area. Transactions in the Mempool are those that users have already initiated from their wallets, but they’re still waiting to be recorded on-chain. Who are they waiting for? The answer is the Sequencer. The Sequencer functions like a miner on an L2 chain, responsible for selecting transactions from the Mempool, organizing them, and packaging them into blocks, which are then relayed back to the Ethereum blockchain, completing the process.
Throughout the process, the Sequencer plays the most crucial role, determining not only which transactions get recorded on the blockchain but also the order in which they are finalized.
In financial applications, the sequence of transactions is highly sensitive. The book Flash Boys documents the real-world lengths the finance industry will go to in order to "be first." If two people each put in $100,000 to buy ETH at the same time, the second buyer often gets a worse deal. After the first purchase, the ETH price may rise slightly, so the second buyer gets a bit less ETH for the same $100,000. With large enough sums and high transaction frequency, these differences can become significant.
The Sequencer has an even greater impact when it comes to whether or not a transaction can even be recorded. If the Sequencer has a blacklist and ignores any transaction from a particular wallet address, those transactions will remain stuck in the Mempool, unable to move forward. Transactions that don’t get recorded on the blockchain are as if they never happened. The Zircuit development team recognized this entry point and created an L2 blockchain that hackers would dread, coining this concept Sequencer Level Security (SLS).
Sequencer Level Security
According to Zircuit’s introduction:
Zircuit protects user security by monitoring the Mempool for malicious transactions, excluding them from blocks. Unlike typical security efforts focused on applications or smart contract levels, Zircuit’s innovative approach begins directly with the underlying Sequencer. Sequencer Level Security provides Zircuit’s blockchain with an additional security layer. We carefully examine each transaction for potential malicious intent before it’s finalized on the L2 blockchain, thus avoiding controversial post-event remedies like hard forks or block rollbacks.
After reading this description, my curiosity was piqued: who exactly is on the Zircuit development team? This statement reflects a very engineering-driven mindset. Engineers, when they see applications and smart contracts vulnerable to hacking, tend to address the issue at a deeper technical level, aiming for a more permanent solution. Unsurprisingly, Zircuit’s co-founders, Jan Gorzny and Martin Derka, are both former employees of the renowned smart contract auditing firm, Quantstamp.
Zircuit’s commitment to security is also evident in its applications. It’s rare to see an application audited by six separate smart contract auditing firms, especially with none of them being Quantstamp. This underscores how seriously the team takes security.
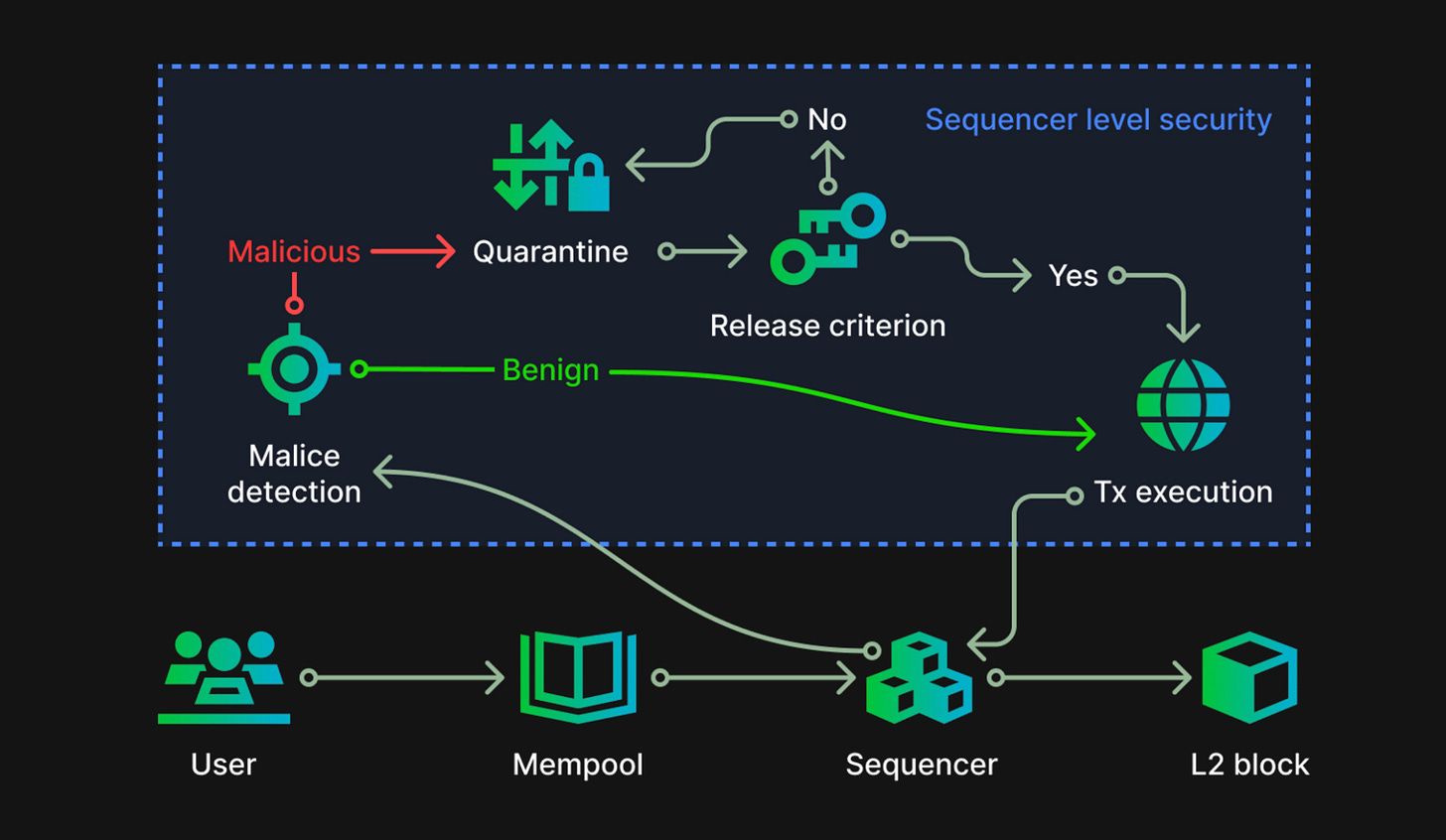
The image below is a diagram of Zircuit’s Sequencer Level Security, showing the complete journey of a transaction from the Mempool, through the Sequencer, and finally to the L2 block. Zircuit’s approach starts at the Sequencer level, where the mechanism operates like antivirus software: when an abnormal transaction is detected, the suspicious transaction is isolated. Since all transactions need to be confirmed on-chain within seconds, human review is not feasible. Hence, Zircuit relies on AI to detect and accurately identify suspicious transactions.
Past hacker behaviors are the foundation for training Zircuit’s AI, enabling it to develop a completely new set of rules (the nature of which remains unknown). This approach reminds me of a past episode when Blocktrend invited DeFiHackLabs co-founder Sun for a recording, where he mentioned that DeFiHackLabs recreates past hacking tactics as simulated exercises for future developers, preventing hackers from succeeding with the same methods. Zircuit, however, directly trains its AI and integrates it into the blockchain’s operational mechanism, ensuring that every application deployed on the Zircuit chain is protected by this mechanism:
Sequencer Level Security is embedded within the Zircuit chain. Therefore, every smart contract deployed on Zircuit benefits from this protective mechanism. However, this mechanism is still a service primarily managed by AI, so it’s not infallible. Developers still need to follow best engineering practices to ensure code security.
In essence, no matter how advanced Zircuit’s AI becomes, there remains a possibility of error. Yet users might be more concerned about potential false positives. Zircuit has established a set of release criteria for its quarantine area.
One such criterion is time, meaning that after a quarantine period, the transaction can be successfully processed on-chain. This creates a cooling-off period, similar to how banks freeze suspicious transactions temporarily, giving the sender time to confirm or providing the victim time to react. Isolating suspicious transactions and then releasing them after a set period enhances asset security.
Additionally, Zircuit simulates each transaction, analyzing its potential impact on the blockchain before deciding to release it. If the simulation identifies the transaction as malicious but finds that the target no longer exists—thus, there’s no potential victim—the transaction is still released. This is akin to bots trying to buy concert tickets: the system isolates the bot transactions immediately, and only after all tickets are sold out are the bots’ orders processed. These would simply become failed orders without causing harm.
The exact mechanisms are much more complex, but this dedicated quarantine zone is Zircuit’s way of protecting user assets. If an application is deployed across multiple blockchains, using the Zircuit version adds an extra layer of security.
However, if Zircuit only promoted its security, it might struggle to stand out in the intense competition. After all, without incidents, users are unaware of potential dangers. Thus, what currently attracts most users to Zircuit is the potential for airdrops.
Abundant Airdrop Opportunities
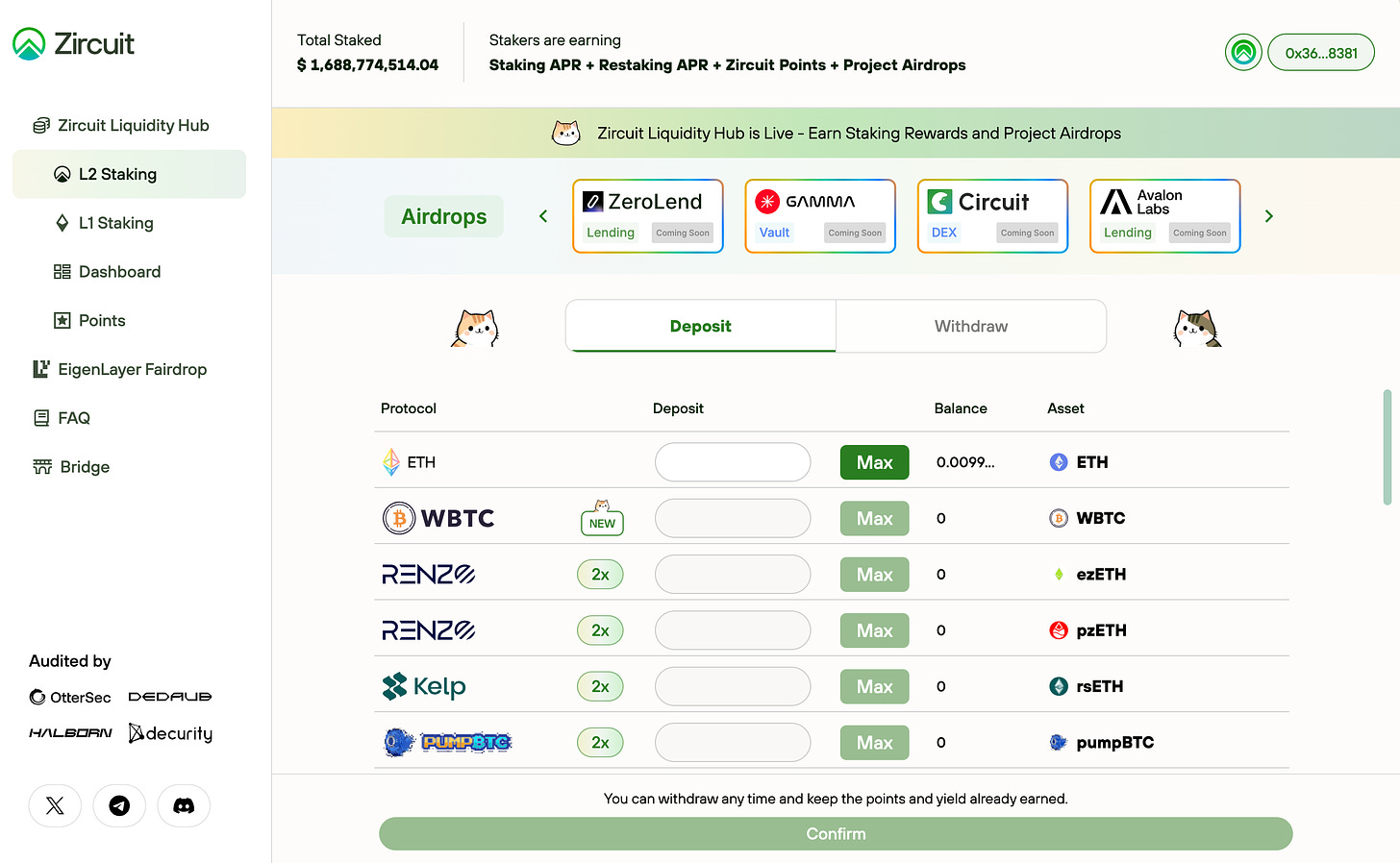
At the beginning of this article, I mentioned walking readers through the Zircuit ecosystem, and here we are at the final section. I suggest using Zircuit’s official cross-chain bridge to transfer around $10 worth of ETH from Ethereum’s main chain (L1) to Zircuit. This amount should be more than enough to cover transaction fees on Zircuit.
The main difference between Zircuit and other L2 ecosystems is that Zircuit is still relatively barren, so it has created a Liquidity Hub. Users who bridge rewards tokens from other chains, like stETH from Lido or ezETH from Renzo, and deposit them in Zircuit’s Liquidity Hub gain potential airdrop opportunities. Zircuit has negotiated with teams planning to conduct token airdrops, setting aside a portion of tokens for users who park their assets in the Liquidity Hub.
Users simply need to place their assets in one location; they won’t miss out on their regular token rewards and can also gain additional airdrop opportunities. It’s perfect for those looking for a low-effort option. In the past, I’d come across similar opportunities that caught my attention, but I always worried about the security risks—what if the liquidity hub gathering everyone’s assets got hacked? However, after researching Zircuit’s security mechanisms, I feel more at ease about participating.
As mentioned at the beginning, if your goal is to maximize airdrop opportunities with security as a priority, then Zircuit might be a great new choice. A demo video is provided below 👇
Blocktrend is an independent media platform sustained by reader subscription fees. If you find Blocktrend's articles valuable, we welcome you to share this piece. You can also join discussions on our member-created Discord or collect the Writing NFT to include this article in your Web3 records.
Furthermore, please consider recommending Blocktrend to your friends and family. If you successfully refer a friend who subscribes, you'll receive a complimentary one-month extension of your membership. You can find past issues in the article list. As readers often inquire about referral codes, I have compiled them on a dedicated page for your convenience. Feel free to make use of them.