Hunting Down North Korean Hackers! Forking Ethereum or Bybit’s Bounty to Turn Insiders Against Them

GM,
I spent the past ten days at the hospital, so there was no new podcast episode released yesterday. The show is expected to resume next week. Now, let’s get to the main topic.
On February 21, North Korean hackers breached Bybit, the world’s second-largest cryptocurrency exchange, stealing a staggering $1.5 billion in a single attack—marking the largest theft in both crypto and financial history 1. Over the past few days, there has been one piece of good news and one piece of bad news.
The good news is that Bybit has secured over 400,000 ETH through loans and direct purchases, not only covering its financial shortfall but also repaying emergency ETH support from other exchanges. Their financial strength is astonishing. The bad news? Nearly one-third of the stolen funds have already been successfully laundered within just a few days. Even if authorities trace the money flow afterward, it may be too late to freeze the assets. Experts estimate that at this pace, the hackers could walk away scot-free in ten days.
In response to this crisis, the community has proposed two drastically different approaches:
- "Reversing time"—forking the Ethereum blockchain.
- A $140 million bounty offered by Bybit to mobilize global efforts in hunting down the hackers.
This unprecedented, multi-front crackdown is testing how the crypto community can combat crime in the so-called “anarchic” nature of blockchain. This article analyzes both response strategies and their potential implications.
Forking Is No Longer an Option
Arthur Hayes, founder of BitMEX, is the strongest advocate for the idea of forking Ethereum to recover the stolen funds. He directly tagged Vitalik Buterin and asked: "In 2016, when The DAO hack resulted in the loss of 3.6 million ETH, you led the community in successfully forking Ethereum. Why not consider doing it again now?"
Forking is an intuitive proposal. Blockchain “time” is determined by consensus. Technically, if all miners (or nodes) worldwide were to revert to a specific block before the hack and restart from there, the 400,000 ETH in the hackers’ possession would lose consensus support, becoming part of a “mosquito chain”—an obsolete and isolated fork. On the new blockchain, the hack would appear as if it never happened.
However, time in the physical world cannot be reversed. Imagine this: if I bought ETH after the hack, but the blockchain’s timeline is rolled back to before the attack, my purchased ETH would simply vanish. Conversely, if I sold ETH for a profit after the attack, then after the fork, I would not only keep the proceeds but also have my ETH reappear in my wallet, allowing me to sell it again. This unfairness would extend across thousands of transactions, creating chaos far worse than the $1.5 billion loss itself. The longer the delay, the higher the cost of reversal.
Ethereum was able to fork successfully after The DAO hack in 2016 for two key reasons. At the time, Ethereum had minimal ties to the real-world economy—it was like a standalone “offline computer.” The DAO smart contract had a 28-day holding period, meaning the hacker couldn’t immediately move the stolen funds, preventing contamination of other transactions. The fork was narrowly targeted at reversing a single exploit, minimizing disruption.
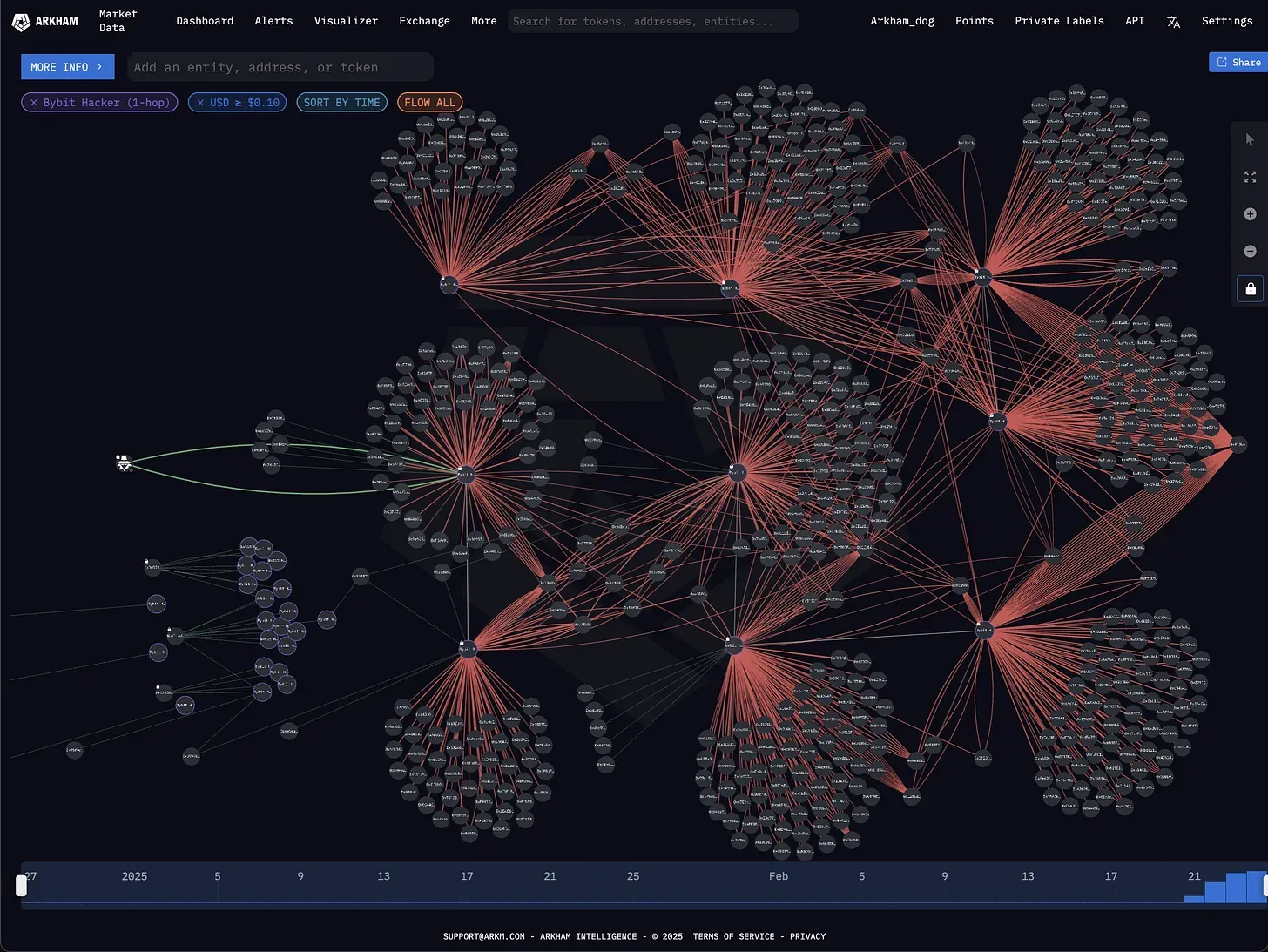
But the Bybit hack is a completely different story. As the stolen assets flow diagram below illustrates, the funds have already been dispersed across thousands of addresses and mixed with countless legitimate transactions. Under these circumstances, forking is no longer a viable option. Even Bybit isn’t hoping to reverse time—it has instead placed a massive bounty to hunt down the hackers.
Economic Defection
The image below is from Bybit’s “Lazarus Bounty” website. This platform provides real-time updates on the movement of stolen funds and the addresses involved in laundering them. Informants who help recover assets and entities that assist in freezing the stolen funds can receive a 10% reward. However, as of now, only 3% of the stolen assets have been frozen, making the situation look grim.
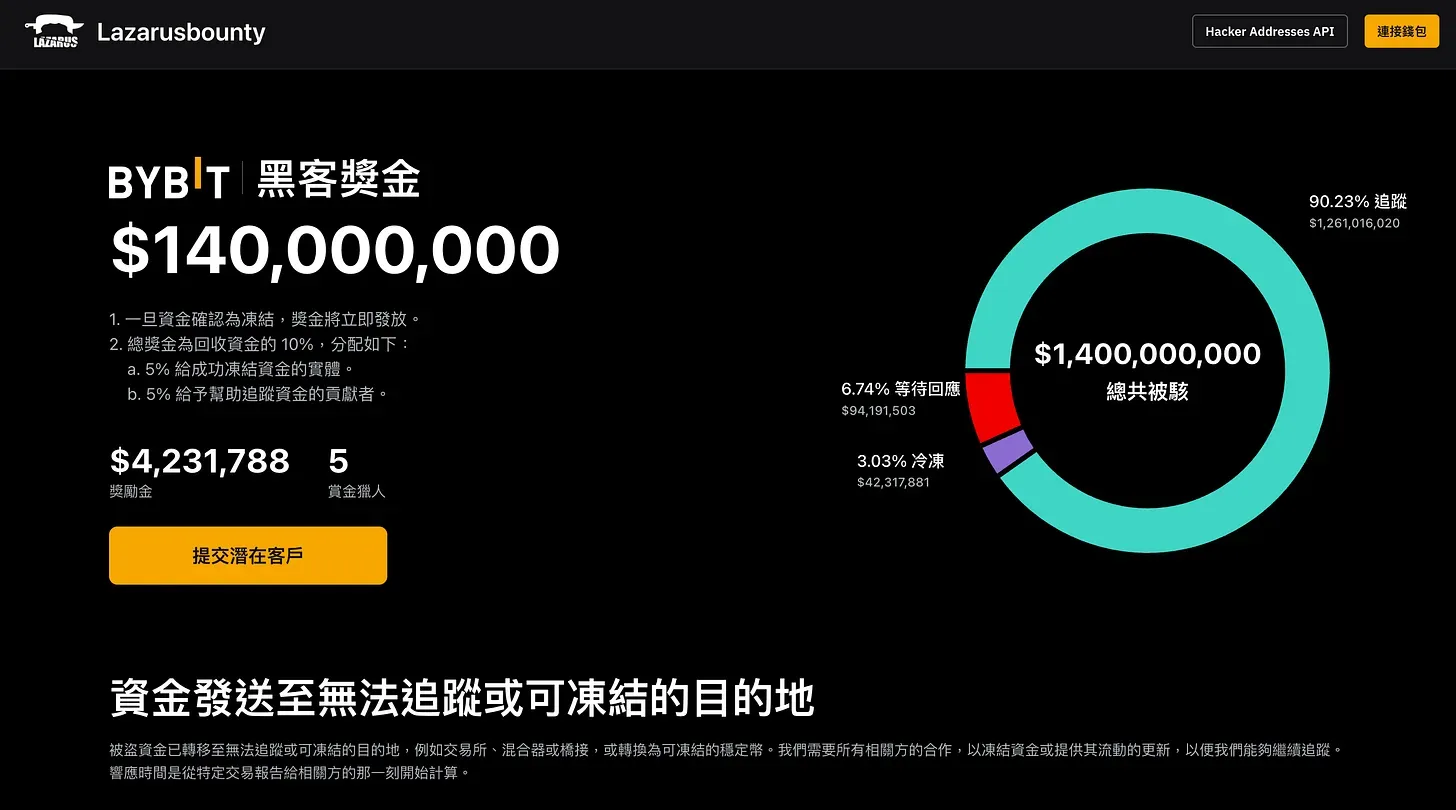
Bybit’s Official Announcement:
Bybit is the world’s second-largest exchange by trading volume. We are launching an API to blacklist suspicious wallet addresses, making it easier for cybersecurity experts to help track and recover stolen funds. This blacklist is collaboratively maintained by white-hat hackers and investigators and will be provided to our partners through an automated interface. Those who successfully intercept stolen assets will receive a 10% reward.
Bybit’s decision to openly declare war on hackers is highly unusual. In the past, most hacking victims have responded passively, at most filing reports with law enforcement. But Bybit is sending a clear message to the attackers: They picked the wrong target.
The 10% bounty isn’t just an incentive for informants—it also raises the cost of laundering stolen funds. Why?
The website highlights six individuals and entities that have assisted in tracking and freezing stolen assets. But the most eye-catching name is the one marked in red—a money-laundering accomplice: eXch Exchange.
eXch is registered in Belize and operates with no Know-Your-Customer (KYC) requirements. It has already received $94 million in stolen funds from the hackers. Bybit quickly detected the transaction and requested eXch to freeze the assets—only to be met with complete refusal.
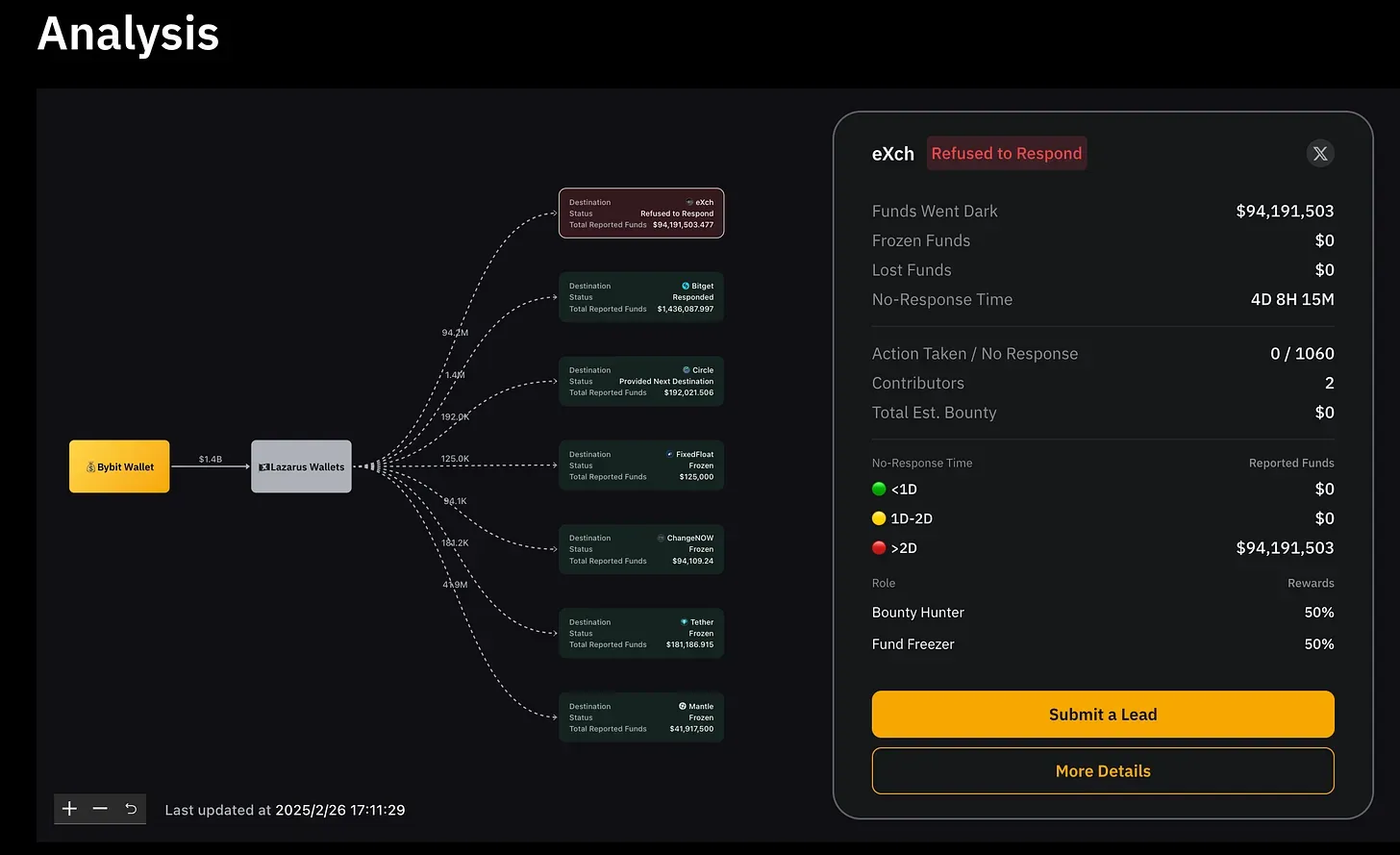
eXch not only refused to assist but also complained that Bybit had been tarnishing its reputation over the past year. Bybit had flagged eXch’s addresses as high-risk, leading to frozen funds when users attempted to transfer assets from eXch to Bybit. "Why should we help them now?" eXch argued.
By prioritizing personal grievances over right and wrong, eXch faced widespread backlash from the crypto community. Meanwhile, blockchain security firm Elliptic noticed an abnormal surge in eXch’s trading volume after the hack, suggesting that hackers were likely laundering funds through the platform. It’s no surprise that Bybit officially labeled eXch as an accomplice and even started a public timer tracking how long the exchange had ignored their request. Yet, despite mounting public pressure, eXch remained uncooperative.
At first glance, this might seem like a childish feud, but eXch’s refusal could also be a calculated business decision. The exchange now faces a dilemma: continue facilitating North Korean hackers’ money laundering or accept Bybit’s 5% bounty for freezing the stolen funds.
Even if eXch chooses to side with the hackers, the cost of laundering their funds will likely increase. If the hackers offer a fee lower than 5%, eXch would have a financial incentive to switch sides and cooperate with Bybit by freezing the assets. This is economic defection in action.
There is precedent for this strategy. In the past, Bitfinex offered up to a 30% bounty to recover stolen BTC. If Bybit raises its reward percentage further, eXch might reconsider its stance, weighing the price against the risks. The hackers could ultimately find themselves in a situation where they’ve successfully stolen the funds—but can’t cash them out.
Antifragile Thinking
The Bybit hack demonstrates that even the most secure multi-signature cold wallets can still fall victim to a well-orchestrated attack. I believe Bybit’s Lazarus Bounty is an attempt to explore a new model for exchange security—shifting from simply preventing attacks to establishing countermeasures after an attack occurs. This is antifragile thinking in action.
North Korean hackers will only continue to refine their techniques, and Bybit won’t be the last exchange to be breached. Instead of assuming that hacks can be entirely prevented, the better approach is to design systems that make it extremely difficult for attackers to profit. Even if hackers manage to steal funds, the fact that every transaction is globally monitored means that as long as the bounty is high enough, intermediaries facilitating money laundering will have a strong financial incentive to betray the hackers.
The bounty system creates the ultimate hacker’s dilemma: even if they successfully infiltrate an exchange, cashing out becomes nearly impossible. When the cost of laundering stolen crypto exceeds the potential profit, hacking ceases to be a worthwhile endeavor. In a decentralized world, the right economic incentives are the most effective form of law enforcement.
Blocktrend is an independent media platform sustained by reader subscription fees. If you find Blocktrend's articles valuable, we welcome you to share this piece. You can also join discussions on our member-created Discord or collect the Writing NFT to include this article in your Web3 records.
Furthermore, please consider recommending Blocktrend to your friends and family. If you successfully refer a friend who subscribes, you'll receive a complimentary one-month extension of your membership. You can find past issues in the article list. As readers often inquire about referral codes, I have compiled them on a dedicated page for your convenience. Feel free to make use of them.