Decentralized Exchange Balancer Hacked! A Chain Reaction of Fires and a DeFi Confidence Crisis

GM,
Starting next week, Blocktrend will take its year-end publishing break. Four articles will be paused, and regular publication will resume on December 2. This is a pre-planned family trip — not a getaway to recover from last week’s loss of funds 😅. But hey, it works out perfectly. Now, onto today’s topic.
Recently, decentralized finance (DeFi) applications have been experiencing a series of meltdowns. Among them, the Balancer hack on November 3 stunned cybersecurity experts worldwide. Although the total loss of $130 million only ranks within the top 30 largest DeFi hacks in history, it has triggered an unprecedented crisis of trust in the DeFi ecosystem.
That’s because Balancer has long been regarded as a model citizen of the DeFi world. Its core code has undergone 11 rigorous security audits conducted by four leading cybersecurity firms, and after launch, it has maintained an ongoing bug bounty program to monitor for vulnerabilities. Anyone who discovers and responsibly reports a bug can earn up to 1,000 ETH as a white-hat reward.
There’s no such thing as absolute security on the internet, but within the industry, it’s widely believed that thorough audits and continuous monitoring can significantly reduce the risk of hacks. Yet the Balancer incident shattered that belief. If even one of the most vetted DeFi protocols can be exploited, people are now asking — whose code can truly be trusted? This article takes you back to the scene of the crime to understand how Balancer was hacked.
The Automatic Currency Exchange Machine
Imagine you’re traveling in Vietnam and you come across a currency exchange machine called Balancer at the airport.
You insert a 1,000 New Taiwan dollar bill, and based on the current exchange rate, the machine should dispense 848,399 Vietnamese dong. Because the machine can only issue banknotes in denominations of 100, it rounds up and gives you 848,400 VND. You’ve made an extra 1 VND, but it’s such a tiny amount that it doesn’t matter — the machine has always worked just fine like this.
For five years, the exchange machine ran smoothly. Then, recently, a clever hacker devised a meticulous plan to exploit this rounding error — and drain all the money inside the machine.
Balancer operates on an automated market maker (AMM) mechanism 1 — meaning exchange rates adjust dynamically based on the supply and demand of assets within the pool. The more people exchange Vietnamese dong for foreign currency, the cheaper the dong becomes; conversely, the more people exchange foreign currencies for dong, the more expensive the dong gets.
The hacker started by supplying a large amount of foreign currency, aggressively buying up all the Vietnamese donginside the exchange machine. As a result, the dong in the pool became scarce, and its price skyrocketed by a factor of 10,000. Suddenly, that same 1,000 TWD bill could only buy 84.8399 VND. But since the machine only dispenses bills in multiples of 100, it rounded up and spit out 100 VND.
See what happened? When the price of VND soared, the rounding error — previously negligible — was magnified exponentially. The hacker gained an extra 15.16 VND every time they exchanged 1,000 TWD. The machine treated this as a minor rounding discrepancy, completely unaware it was being drained. By repeating the process, the hacker forced the machine to issue vast amounts of VND, which they then swapped for other currencies inside the machine — emptying it completely.
The image below shows the on-chain transaction records from November 3, when the attack occurred. In a single transaction, the hacker executed multiple smart contract operations, draining Balancer’s liquidity pools in one swoop and stealing approximately $130 million in total.
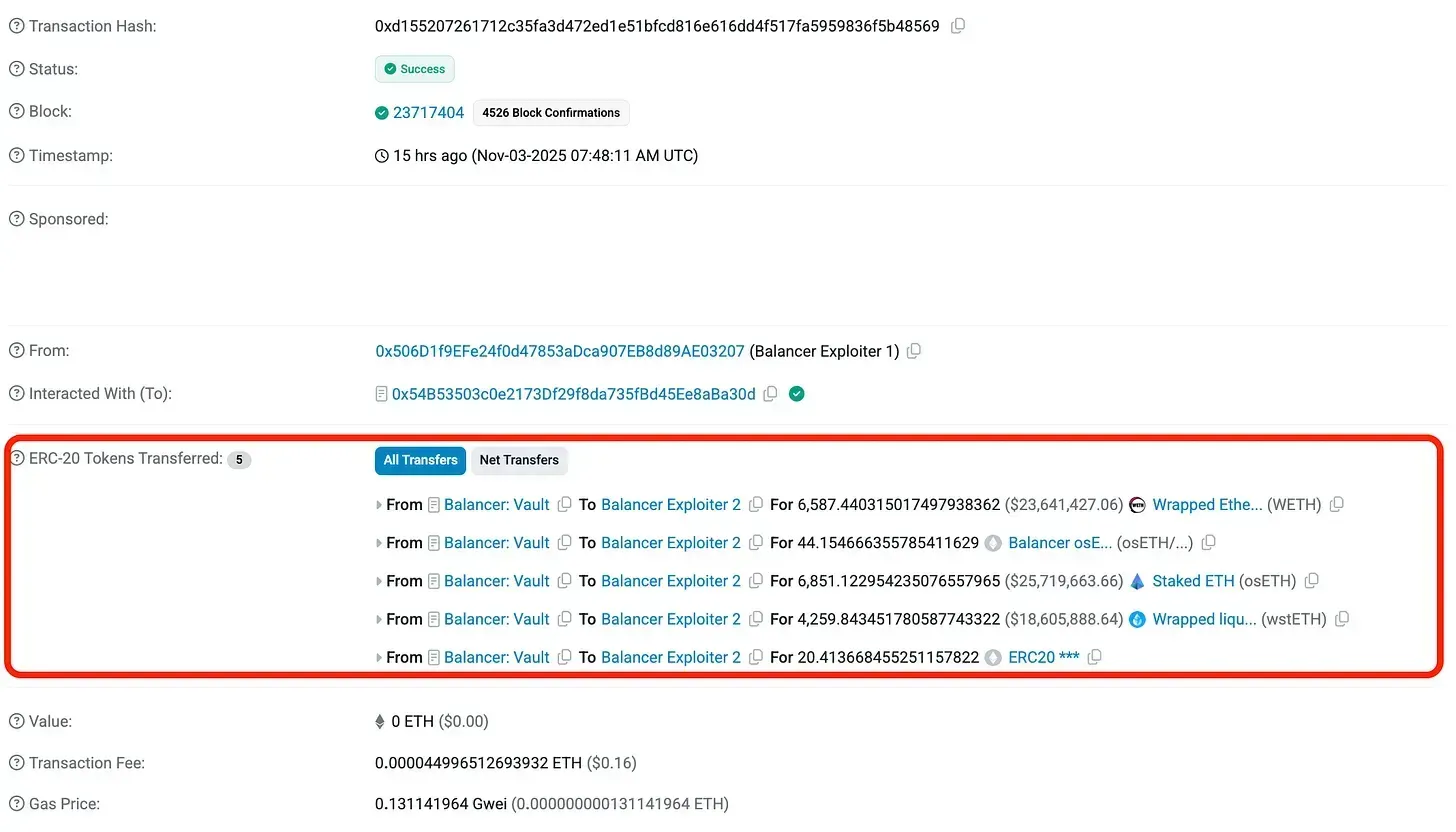
Alarms went off across the blockchain immediately. Since every on-chain transaction record is public in real time, cybersecurity firms like Check Point and PeckShield quickly detected abnormal fund outflows from Balancer through their automated monitoring systems and alerted the development team right away.
The Balancer codebase includes an “emergency pause” function, designed to temporarily halt operations during major incidents to prevent further losses. But here’s the catch — the hacker wasn’t targeting the latest Balancer V3, but the older V2 version that had been running for years. When developers tried to hit the pause button, they discovered it no longer worked — the permissions had expired, rendering the control useless. The “exchange machine” had become a kite with its string cut, and everyone could only watch helplessly as the liquidity pools were drained.
In most hacks, that would already be the worst-case scenario. But for Balancer, this was just the beginning of a chain reaction.
A Chain of Burning Ships
Over the years, many emerging DeFi projects had treated Balancer V2 as a gold standard, building upon its open-source codebase. Nearly 30 DeFi applications were derived from it. Unfortunately, that meant the attack quickly escalated into a “chain fire”, spreading far beyond Balancer itself.
For example, Beets.fi, the largest decentralized exchange (DEX) on the Sonic blockchain, proudly stated in its documentation that its own code was forked from Balancer V2. When it launched its governance token, Beets even retroactively airdropped tokens to Balancer users as a gesture of appreciation. The intention was to highlight that it was built on battle-tested code, supposedly giving users confidence. No one expected the “model student” to crash so spectacularly.
The hacker didn’t just stop at Balancer — they also targeted forked protocols using the same vulnerability, including Beets, which suffered similar losses.
In response, developers on the Sonic blockchain tried to outsmart the attacker by tweaking the gas fee mechanism, freezing the gas balance within the hacker’s wallet. Even if the hacker managed to steal funds, they wouldn’t have enough gas to move them.
Meanwhile, BEX, the second-largest DEX on the Berachain blockchain — also forked from Balancer V2 — was breached simultaneously. The Berachain team took an even more drastic step: fearing that the losses would continue to grow, they shut down the entire blockchain, sacrificing the system to stop the attack. The extreme move worked — they eventually recovered $12.8 million from the hacker.
On the Polygon network, validators chose to block all Balancer V2-related transactions, effectively freezing any assets the hacker tried to move, as no validator would include their transfers on-chain.
However, not all blockchains were willing to intervene. The Ethereum mainnet is inherently resistant to freezing, and while Arbitrum, Base, and Optimism theoretically have the ability to block transactions, they chose not to act during this incident.
This naturally reignited debates over decentralization. Some praised the quick response of those blockchains that stepped in, arguing it protected users’ assets and stopped the hacker in time. Others criticized these actions as violating the censorship-resistant ethos of blockchain — that even malicious transactions should remain beyond interference.
To be fair, this is a moral and philosophical dilemma. If it were your own hard-earned savings at stake, how many people could truly stand firm in defense of blockchain neutrality and censorship resistance? Yet if blockchains intervene now, what’s to stop regulators from later patting these same teams on the shoulder and saying, “You know how to do it — just cooperate a little next time”?
DeFi’s Crisis of Confidence
I believe the Balancer hack has ignited three major discussions — triggering what might be the most severe crisis of confidence in DeFi to date:
- Open source becoming a vector for contagion
- What does it mean for a smart contract to be “secure”?
- How far should censorship resistance go?
The open-source ethos in DeFi encourages developers to stand on the shoulders of giants, allowing innovation without reinventing the wheel. Yet this incident exposed the dark side of that philosophy — the terrifying “chain-fire” effect.
In traditional finance, Bank A would never directly copy the core system of Bank B. But in DeFi, forking existing codeis commonplace. That creates a new pathway for risk transmission. As a result, when Balancer was hacked, a seemingly unrelated blockchain like Berachain, worlds away, had to shut down its entire network to contain the impact. This interconnected fragility sets the Balancer attack apart from past exploits.
In previous hack incidents, people would often shrug and say: “You should’ve done your own research (DYOR) before using it.” But this time, Balancer had done everything right — it hired four top-tier cybersecurity firms to conduct 11 separate audits of its codebase — and it still fell victim to a devastating exploit.
When people later revisited those past audit reports, they discovered that as early as 2020, the security firm OpenZeppelin had already flagged the rounding error logic in Balancer’s code. At the time, their assessment stated: “Under most normal conditions, these rounding errors are negligible and not exploitable. However, under extreme conditions, they could be profitably manipulated.”
Ultimately, OpenZeppelin gave Balancer’s contracts an overall evaluation of “well-written and clear”, with the rounding error categorized as a “low-severity issue.”
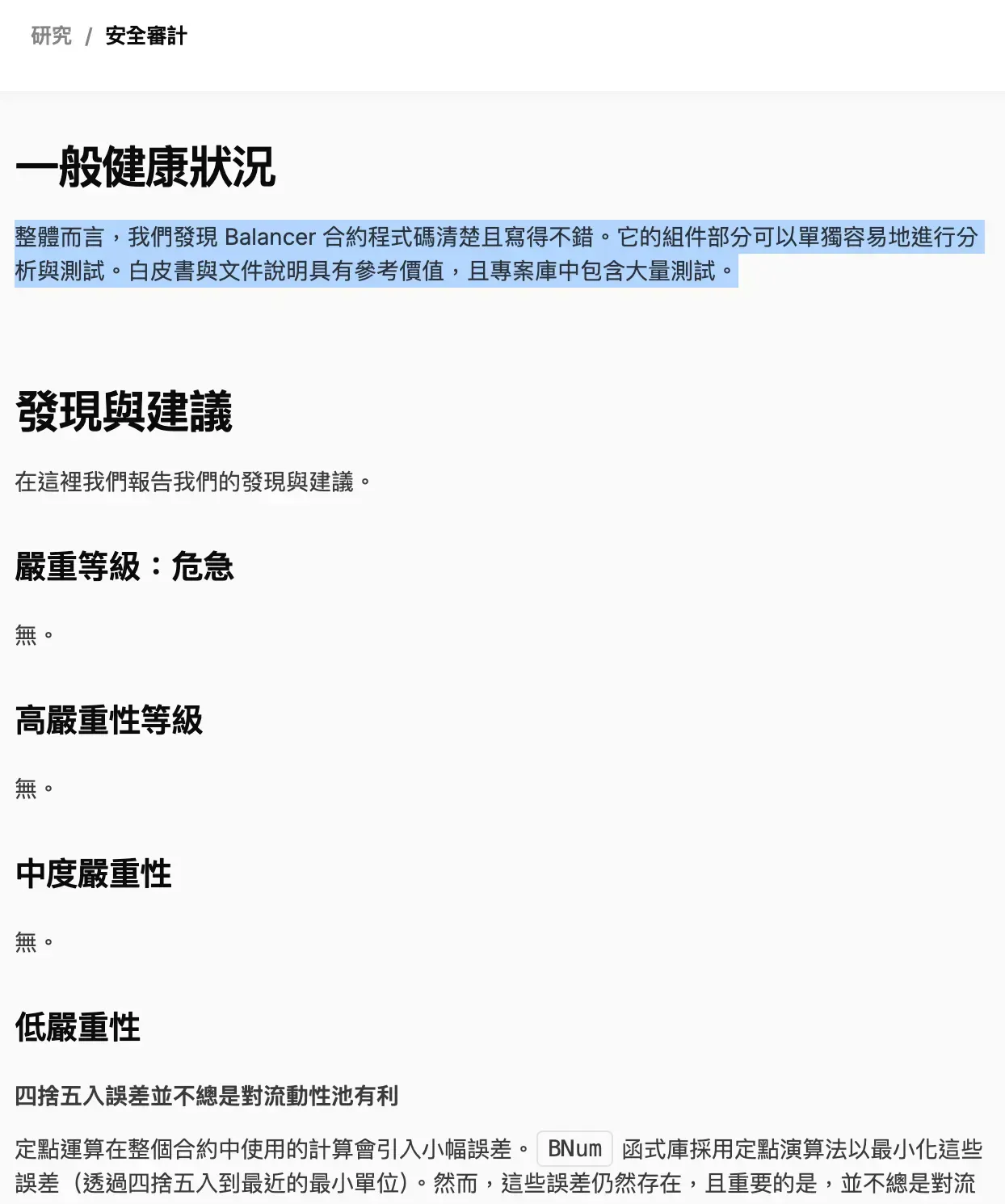
In 2021, another leading cybersecurity firm, Trail of Bits, mentioned the same issue in its audit report — but classified it as “Undetermined Severity.” In other words, while they recognized that the code carried a potential risk, they could not determine whether it was actually exploitable by hackers.
Both firms are highly respected in the industry, having seen every kind of obscure codebase and ingenious exploit imaginable. If even experts like them couldn’t be sure whether this design flaw was fatal, how could ordinary users possibly have spotted it?
After the incident, some began to question whether code audits were still reliable. The more troubling reality, however, is that no one yet knows how to prevent a similar attack from happening again. Identifying a problem without knowing how to fix it — that’s what has turned this hack into a full-blown DeFi confidence crisis.
When people can’t mitigate risk, the only rational move is to withdraw their funds — or move to blockchains that claim to “proactively protect users.”
Most blockchains only react after disaster strikes — hurriedly coordinating validators to freeze transactions and then facing the painful dilemma between decentralization and censorship. But last year, Blocktrend covered one project that chose a different path: the Zircuit blockchain 2 3.
Both Zircuit co-founders came from the audit firm Quantstamp. Having witnessed countless post-mortems and the helplessness that follows each exploit, they designed Zircuit with built-in “antivirus” features from day one. Using AI to analyze transaction behavior and learn from past attack patterns, Zircuit automatically isolates suspicious activity — effectively declaring from the start that its blockchain stands firmly against hackers.
Yet, the question of how to balance risk control with user autonomy remains unanswered. In the documentary “Vitalik: The Ethereum Story,” the host asked Ethereum founder Vitalik Buterin: “Do you think you should take responsibility for the hacks that happen on Ethereum?” Vitalik replied with a metaphor: “Fire can keep you warm, but if you don’t control it properly, you can get burned.”
DeFi developers have learned to use fire — but they still haven’t mastered how to use it safely.
1 Automated Market Makers (AMMs): Democratizing Trading Profits and How to Avoid Impermanent Loss
2 Predictable Airdrops! How Zircuit Is Building the Blockchain Hackers Hate Most